The Secrets Management Checklist for Your Evolving Cloud Journey
In this blog, we will explore the secrets management checklist for your evolving cloud journey.
As enterprises transition deeper into the cloud journey, securing sensitive credentials—known as secrets—becomes critical. Whether you’re just starting with cloud adoption, standardizing platforms, or scaling across hybrid and multi-cloud setups, robust secrets management is vital to reduce risk.
Misconfigurations and compromised credentials are making cloud environments more vulnerable to attacks. In fact, analysts predict that nearly all cloud breaches by 2027 will stem from these weaknesses. This checklist offers best practices across three stages of cloud maturity—Adopting, Standardizing, and Scaling—to guide your secrets management strategy.
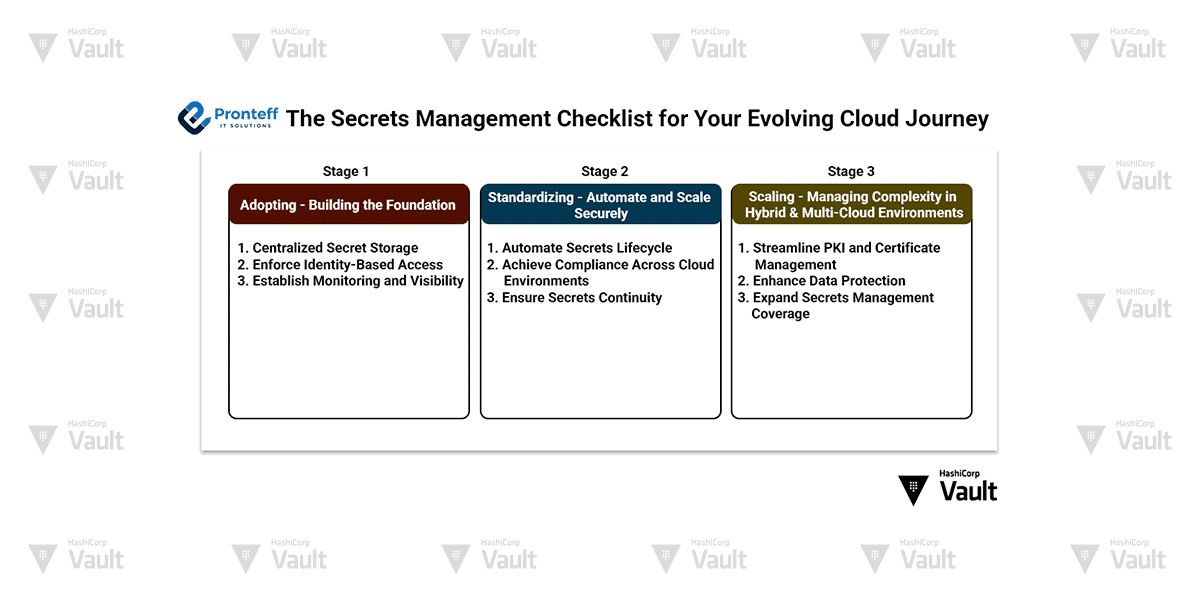
Stage 1: Adopting — Building the Foundation
Organizations in the adoption phase are exploring the cloud’s benefits. Processes are often manual and decentralized, making it crucial to establish a baseline for securing secrets.
1. Centralized Secret Storage
✅ Securely manage all credentials by storing them in a centralized secrets vault, minimizing the risk of “secret sprawl” and reducing potential exposure.
2. Enforce Identity-Based Access
✅ Use identity-based authentication and authorization for both human and machine users.
✅Enforce the principle of least privilege to limit access to sensitive data as much as possible.
3. Establish Monitoring and Visibility
✅ Track secret usage through centralized dashboards.
✅ Continuously scan for hardcoded or exposed secrets across codebases and environments.
✅ Integrate third-party monitoring tools for unified visibility and faster threat detection.
Stage 2: Standardizing — Automate and Scale Securely
At this point, organizations are moving towards consistent platforms and automated pipelines. With growing cloud footprints, compliance and automation take center stage.
4. Automate Secrets Lifecycle
✅ Automate secret injection for legacy systems using modern secrets managers.
✅ Use dynamic, time-limited secrets that are created on-demand (just-in-time) for enhanced security.
✅ Set up auto-rotation schedules to prevent stale or forgotten secrets from becoming risks.
5. Achieve Compliance Across Cloud Environments
✅ Automate detection of unsecured secrets through continuous scanning.
✅ Integrate secrets scanning into CI/CD pipelines to catch issues before deployment.
✅ Use namespaces or team-specific access controls for better segregation.
✅ Enable audit logs for every secret transaction to ensure traceability and alert on anomalies.
6. Ensure Secrets Continuity
✅ Ensure consistent replication of secrets across regions and zones to prevent service interruptions.
✅ Implement high availability (HA) and backups for your secrets management infrastructure to minimize downtime and data loss.
Stage 3: Scaling — Managing Complexity in Hybrid & Multi-Cloud Environments
As enterprises mature, they must manage secrets across hybrid infrastructure, multiple clouds, and growing teams—without compromising security.
7. Streamline PKI and Certificate Management
✅ Consolidate public key infrastructure (PKI) into a unified platform to reduce errors and eliminate long-lived certificates.
✅ Standardize key and certificate automation across providers like AWS KMS, Azure Key Vault, and Google Cloud KMS.
8. Enhance Data Protection
✅ Use advanced techniques like tokenization, data masking, and format-preserving encryption (FPE) to secure secrets and sensitive data both in transit and at rest.
9. Expand Secrets Management Coverage
✅ Extend secrets automation across all platforms—cloud, on-premises, and hybrid environments—to maintain consistency and governance at scale.
Ready to Mature Your Secrets Management?
Cloud security isn’t just about tools—it’s about evolving your practices as your architecture grows. From startups to large enterprises, secrets management must adapt to new risks, operational models, and compliance demands.
If your organization is exploring a modern approach to secure and govern multi-cloud environments, let’s talk. Explore how Pronteff and our partners like IBM and HashiCorp, help enterprises implement scalable, policy-driven secrets management solutions.