CERT-In & RBI Incident Response with Vault
In this blog, we will learn about CERT-In & RBI Incident Response with Vault.
In India’s banking sector, the Indian Computer Emergency Response Team (CERT-In) and the Reserve Bank of India (RBI) have set strict mandates to ensure that financial institutions can respond quickly and effectively to security incidents. These requirements are designed to minimize damage from data breaches, credential theft, and insider threats by enforcing fast, auditable, and automated incident response processes.
For banks, this means being able to detect compromised credentials in real time, revoke them instantly, rotate secrets without delay, and generate detailed incident reports for regulatory submission. Manual processes are too slow for modern threat environments—automation and centralized controls are essential.
HashiCorp Vault provides a unified platform to manage, rotate, and revoke secrets while maintaining immutable audit logs. By integrating with banking applications, Vault enables compliance with CERT-In and RBI mandates while also improving operational resilience.
CERT-In Guidelines Where Vault Adds Value
- Maintain logs for all systems – Vault’s audit devices produce tamper-proof logs for every operation.
- Ensure logs are retrievable within 72 hours – All records are instantly accessible for investigations.
- Implement strict access controls – Role-based access control (RBAC) and fine-grained policies restrict access.
- Respond quickly to credential compromise – Dynamic secrets can be revoked instantly, rendering them unusable.
- Monitor API and system access – Vault integrates with SIEM solutions for continuous monitoring.
- Securely manage certificates and keys – PKI secrets engine handles issuance, rotation, and revocation.
- Enable multi-factor authentication – Supported through integration with external identity providers.
- Encrypt sensitive data – Achieved through the Transit and PKI engines.
- Support incident reporting – Audit evidence is ready for submission to regulators.
- Secure third-party access – Scoped, short-lived credentials for vendors and partners.
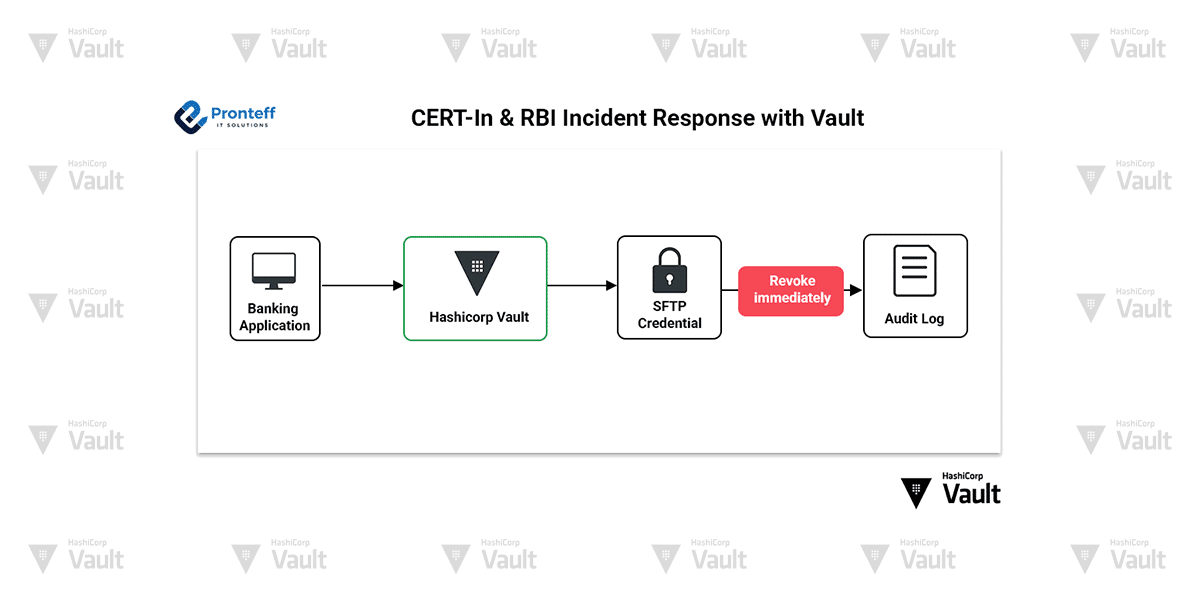
Technical Banking Use Case – Instant Revocation in CBS Jobs
Scenario: A Core Banking System (CBS) batch job uses an SFTP credential that is suspected to be compromised.
Vault Implementation:
- Configure Vault to generate short-lived SFTP credentials dynamically before each batch job.
- If a breach is suspected, revoke the credential immediately via the Vault API—making it unusable within seconds.
- Use Vault Agent to automatically fetch new credentials for the next scheduled job.
- Maintain detailed audit logs that record the credentials creation, usage, revocation, and replacement.
This approach not only meets CERT-In and RBI’s incident response mandates but also reduces operational downtime and the risk of further compromise.