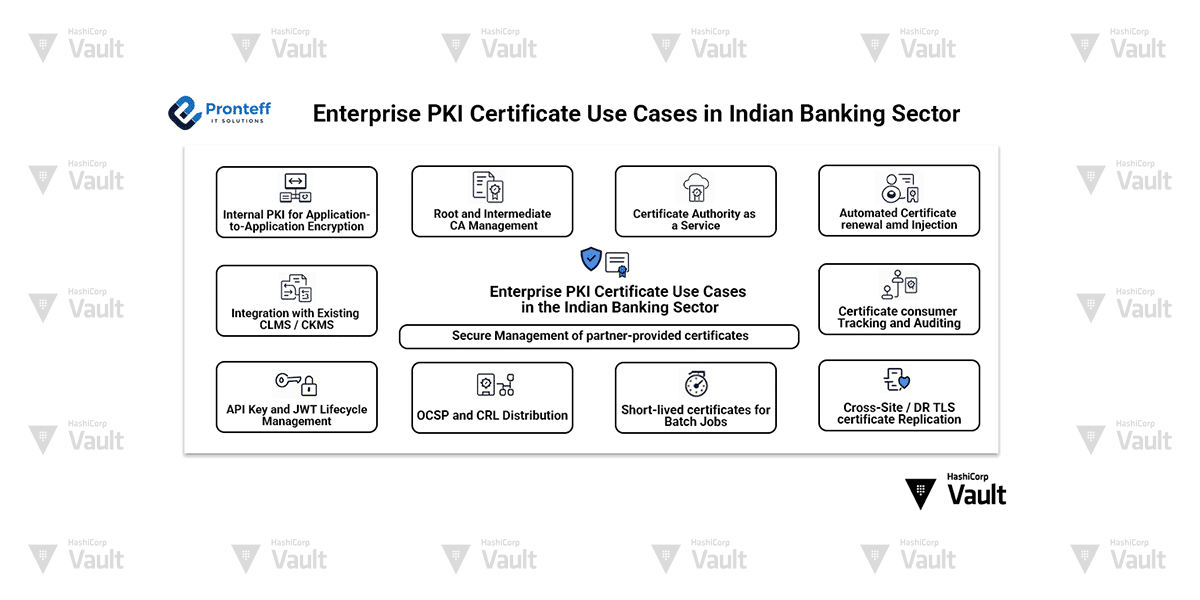
Enterprise PKI Certificate Use Cases in the Indian Banking Sector
In today’s regulated and security-conscious banking environment, Public Key Infrastructure (PKI) plays a foundational role in securing communications, applications, APIs, and user identities. HashiCorp Vault Enterprise offers advanced PKI functionalities that can replace or integrate with traditional CLMS (Certificate Lifecycle Management Systems) and CKMS (Cryptographic Key Management Systems). Below is a detailed list of practical use cases and how they apply in the context of Indian banks.
Internal PKI for Application-to-Application Encryption
Issue short-lived internal TLS certificates for mutual TLS (mTLS) between microservices or applications. Automates rotation, revocation, and delivery using Vault Agent or Envconsul.
Root and Intermediate CA Management
Set up bank-owned root and intermediate certificate authorities for internal PKI usage, fully isolated from third-party external CAs. This supports internal trust chains for non-public workloads.
Certificate Authority as a Service
Provide on-demand certificate issuance to DevOps and application teams using Vault namespaces and custom roles. Supports self-service issuance with fine-grained access controls.
Integration with Existing CLMS / CKMS
Vault can co-exist with or gradually replace traditional CLMS/CKMS tools by integrating via REST APIs or using cert export/import flows. Supports compatibility with Thales, Entrust, DigiCert, and more.
Certificate Expiry Monitoring and Alerting
Monitor issued certificates with built-in TTL tracking. Integrate with Prometheus/Grafana, email alerts, and SIEM tools to proactively warn about upcoming expiries.
Automated Certificate Renewal and Injection
Automatically renew certificates before expiry and inject them into workloads using Vault Agent templates or sidecar containers. Useful for Java apps, NGINX, Apache, etc.
API Key and JWT Lifecycle Management
Replace static API keys and long-lived tokens with dynamic, time-bound secrets (JWT, API keys) managed via Vault’s KV, Transit or Identity Secrets Engines.
Secure Management of Partner-Provided Certificates
Store and control access to externally provided partner certificates securely in Vault KV with encryption, audit logging, and RBAC policies.
Certificate Consumer Tracking and Auditing
Use Vault audit logs and metadata tagging to track which system, team, or user issued or consumed a certificate. Supports accountability and governance in regulated environments.
OCSP and CRL Distribution
Support Online Certificate Status Protocol (OCSP) and Certificate Revocation Lists (CRL) for revoked cert lookup. Vault can host these endpoints directly or publish them to external services.
Short-lived Certificates for Batch Jobs
Issue ephemeral certs valid for a few minutes for backend jobs (e.g., CBS jobs, reconciliation tasks) that need TLS auth during limited time windows.
Cross-Site / DR TLS Certificate Replication
Banks operating across multiple data centers (e.g., Production and Disaster Recovery) can leverage Vault Enterprise’s replication capabilities or synchronize certificate issuance to maintain a consistent PKI policy and centralized certificate management.
Central PKI for Open Banking APIs
Vault can be used to manage certificates for open banking APIs, ensuring compliance with IndiaStack and RBI regulatory standards. Supports secure partner onboarding and mTLS auth.
End-User Certificate Issuance (Optional)
Though less common, banks may issue digital certificates for employees or third-party agents for secure email, VPN, or auth — Vault supports such issuance with audit trails.
CLI and Script-Based Certificate Lifecycle Automation
Using Vault’s CLI and API, banks can streamline certificate issuance, renewal, and revocation in legacy environments, seamlessly integrating with shell- or batch script-based systems.
All of the above use cases are demoable using HashiCorp Vault Enterprise in a lab setup. Banks can start small with one or two internal use cases and expand to a centralized PKI and secrets platform.