Secrets Lifecycle in a Core Banking Setup Using HashiCorp Vault
In the modern financial services landscape, core banking systems sit at the heart of digital operations—handling customer accounts, transactions, and integrations with third-party systems like UPI, SWIFT, and digital lending APIs. With such critical responsibilities, managing secrets and credentials—securely and efficiently—is not just a security requirement; it’s a regulatory mandate.
Why Secrets Lifecycle Matters in Banking
Banking environments are complex ecosystems with:
- Hundreds of batch jobs, CBS services, and middleware components.
- Thousands of credentials, certificates, tokens, and API keys.
- Integration with legacy systems, cloud-native apps, and regulatory interfaces.
Without a centralized system:
- Secrets are hardcoded or manually rotated.
- Expired certificates break services.
- Unauthorized access risks go undetected.
- Compliance audits become nightmares.
Enter HashiCorp Vault: A Unified Secrets Platform
HashiCorp Vault provides a zero‑trust method for managing and protecting secrets. It centrally stores, accesses, distributes, and rotates secrets across dynamic environments—on-premise, cloud, and hybrid.
Core Features for Banking Use Cases:
- Dynamic secrets (DB credentials, tokens) that auto-expire.
- Automated certificate issuance and renewal using PKI.
- Audit logs for every secret access and lifecycle event.
- Fine-grained access controls via namespaces and policies.
- Vault Agent & Template to auto-inject secrets into apps.
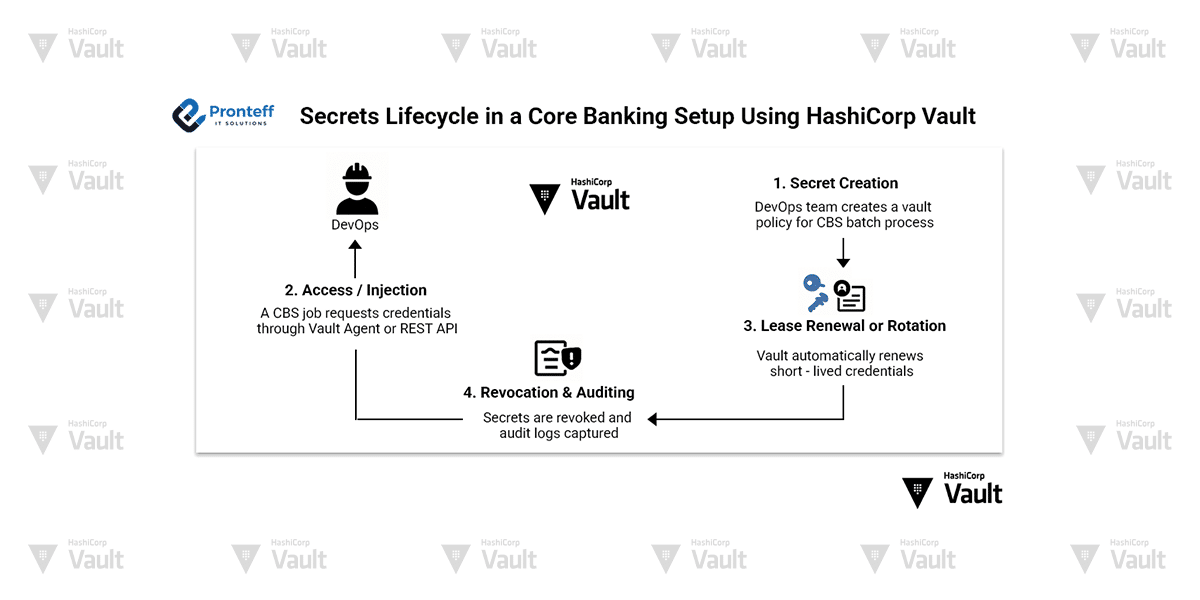
The Secrets Lifecycle in Core Banking (Illustrated)
- Secret Creation
DevOps team creates a Vault policy for the CBS batch process. Vault is configured to generate dynamic PostgreSQL/Oracle credentials per request.
vault write database/roles/cbs-readonly \
db_name=cbsdb \
creation_statements="GRANT SELECT ON accounts TO "{{name}}";" \
default_ttl="1h" \
max_ttl="24h"
- Access/Injection
A CBS job requests credentials through the Vault Agent or REST API. Vault generates database credentials on the fly, assigning them a short time-to-live.
vault read database/creds/cbs-readonly
- Lease Renewal or Rotation
Vault automatically renews the lease if the job is still active. Once the TTL expires, the user account is revoked and deleted from the database. No manual cleanup needed. No long-lived passwords.
- Revocation & Auditing
If a service is compromised or no longer trusted, secrets can be revoked instantly.
vault lease revoke database/creds/cbs-readonly/[lease_id]
Every read, write, and revoke event is captured in the Vault audit logs, ready for compliance checks.
Example: Automating Certificate Lifecycle
Vault’s PKI secrets engine can:
- Issue short-lived certificates dynamically.
- Auto-renew using Vault Agent with renewal hooks.
- Please keep a record of all generated certificates along with their expiration details.
How Banks Benefit
| Benefit | Description |
|---|---|
| Security | No hardcoded credentials, secrets are ephemeral. |
| Compliance | Full audit trail for every secret. |
| Automation | Integrates with CI/CD pipelines and orchestrators. |
| Efficiency | Secrets auto-rotate, reducing ops overhead. |
| Flexibility | Works with Oracle, PostgreSQL, MQ, APIs, and more. |
Ready for Your Bank?
Pronteff’s certified Vault experts can:
- Evaluate your CBS and overall infrastructure to determine the maturity of your secrets management lifecycle.
- Design an implementation blueprint.
- Run PoCs and secure pilot rollouts.
- Integrate Vault with IBM Cloud Pak, OpenShift, and CI/CD pipelines.
Get in touch for a free PoC tailored to your banking use case.