Vault for PCI-DSS & ISO 27001 Compliance in Banking
In this blog, we will learn about the vault for PCI-DSS & ISO 27001 compliance in banking.
Banks in India handling payment card data must comply with PCI-DSS and ISO 27001 to ensure data security, reduce fraud risk, and protect customer trust.
These standards cover a wide range of security practices, from network defenses to encryption and access control.
HashiCorp Vault addresses the secrets management, encryption, access control, and audit parts of these requirements—helping banks achieve compliance faster and with stronger automation.
The 12 PCI-DSS Requirements
- Installing and managing firewall settings – Outside the scope of Vault.
- Do not use vendor-supplied defaults – Partial: Vault enforces unique, rotated credentials.
- Protect stored cardholder data – Vault encrypts PANs, supports tokenization.
- Encrypt transmission of cardholder data – Vault manages TLS/SSL certificates.
- Deploy and keep antivirus tools up to date – Outside Vault’s responsibilities.
- Develop and maintain secure systems – Partial: Vault integrates with CI/CD for secret injection.
- Restrict access to cardholder data – RBAC and policies enforce least-privilege.
- Assign a unique ID – Partial: Vault authentication ensures a unique identity.
- Limit direct physical access – Beyond Vault’s scope.
- Record and oversee access activities – Maintains tamper-proof audit logs.
- Regularly test security systems – Not Vault’s scope.
- Maintain an information security policy – Partial: Vault enforces credential-related policies.
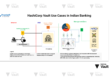
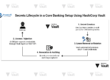
Technical Banking Use Case – Payment Gateway Card Data Protection
Scenario: A bank’s payment gateway must handle and store encrypted Primary Account Numbers (PANs) while ensuring only authorized services can decrypt them.
Vault Implementation:
- Use Transit Secrets Engine to encrypt PANs before they enter the database.
- Store ciphertext in the transaction DB.
- Configure Vault policies to allow only payment processing microservices to decrypt PANs.
- Enable audit device in Vault to log each decryption request with timestamp, service ID, and IP address.
- Rotate encryption keys periodically without re-encrypting existing data using Vault’s key versioning.