Container deployment patterns validated for zero trust
In this blog, we will learn how container deployment patterns can be validated for zero trust.
Confidential computing leverages a Trusted Execution Environment (TEE) to protect data during processing, providing encryption not only for stored and transmitted data but also for data actively in use. Building on this approach, Confidential Containers (CoCo) enhance security by incorporating TEEs into Kubernetes deployments. By enabling TEEs at the pod level, workloads are strongly isolated not only from other workloads but also from cluster administrators.
The Initial Challenge
The main challenge in adopting Confidential Containers is the complexity involved in setting them up. Although modifying a pod manifest to deploy a confidential container is just a single-line change, successful implementation requires configuring multiple components across clusters. Red Hat now offers support for Confidential Containers on Microsoft Azure through Red Hat OpenShift Sandboxed Container Operator v1.9+, along with remote attestation capabilities provided by the Red Hat build of Trustee.
This article explores how validated patterns can streamline the adoption of Confidential Containers by focusing on three key objectives:
- Simplifying the deployment process using OpenShift Sandboxed Containers Operator and Trustee on Azure.
- Providing a standardized, declarative framework that supports deployments following best practices.
- Demonstrating application deployment using CoCo.
Understanding Validated Patterns
Validated patterns are pre-tested, reusable code architectures designed for multi-cloud and hybrid cloud deployments. These patterns are continually tested against the latest versions of operators and OpenShift releases within Red Hat’s continuous integration (CI) framework. Once mature, they’re incorporated into Red Hat’s repository of tested deployment solutions.
Each validated pattern presents a real-world business use case through Kubernetes resources such as Helm charts, Kustomize configurations, and basic objects. These patterns define a hybrid cloud infrastructure comprehensively, covering services, configuration, and supporting elements. They support highly reproducible deployments, ideal for GitOps-driven operations at scale.
Why Adopt Validated Patterns?
Deploying complex solutions often involves multiple steps, where inconsistencies or errors can introduce inefficiencies. Validated patterns address this by:
- Delivering deployment processes as code using GitOps.
- Offering templates that can be modified for specific requirements.
- Ensuring high reproducibility, making it easier to operate at scale.
- Encouraging community collaboration since all repositories are open source.
- Allowing easy customization by swapping components within the configuration.
- Being continuously tested as part of Red Hat’s CI system.
- Providing a comprehensive “batteries included” solution to get started quickly.
In this article, a validated pattern is utilized to illustrate a streamlined approach for deploying Confidential Containers.
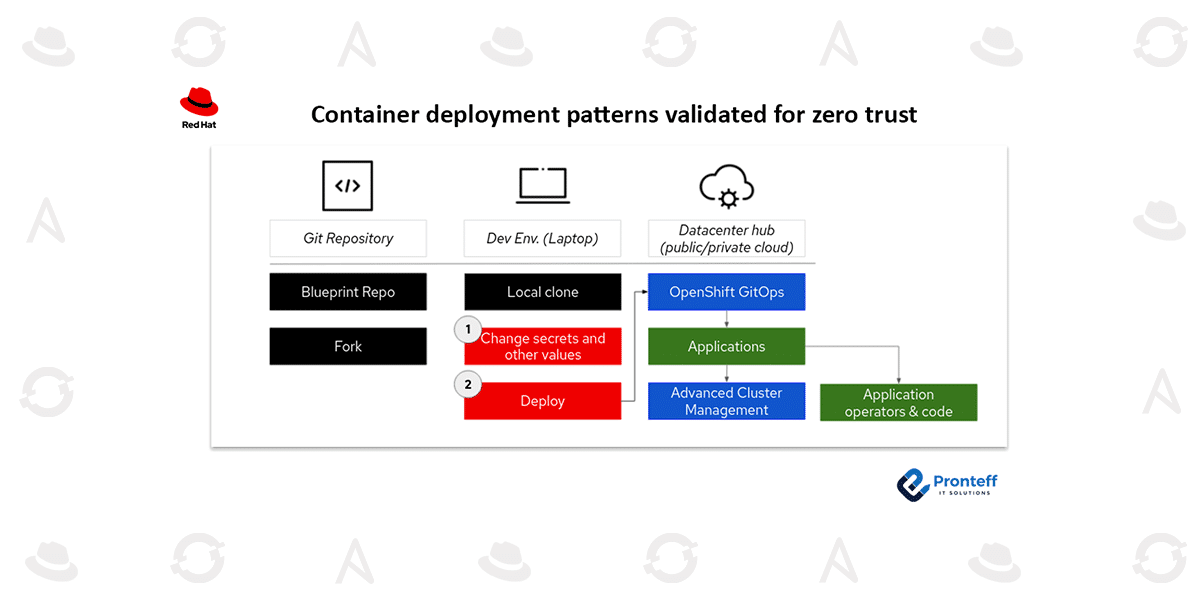
How to Deploy a Pattern
Best practices for deploying validated patterns include:
- Forking the pattern’s Git repository to control and adapt it.
- Using a developer environment with tools like `oc`, `Git`, and `Podman` installed.
- Configuring a new OpenShift cluster that is overseen and controlled by the pattern operator.
This setup ensures that the validated pattern has full control over the cluster’s resources, simplifying deployment to a single starting point.
Confidential Containers in Action
Built on Kata Containers, Red Hat’s sandboxed containers provide the foundation for running Confidential Containers. These containers operate within isolated hardware enclaves to protect data and code from unauthorized access, even from privileged administrators.
Confidential computing enhances data security by utilizing hardware-based solutions to create isolated and protected environments.
This ensures workloads are shielded from tampering or exposure during execution.
CoCo seeks to establish a standardized approach for confidential computing within Kubernetes pods, allowing users to deploy workloads with familiar tools without requiring deep expertise in the underlying security mechanisms.
For more details, you can explore Red Hat’s OpenShift confidential containers solution.
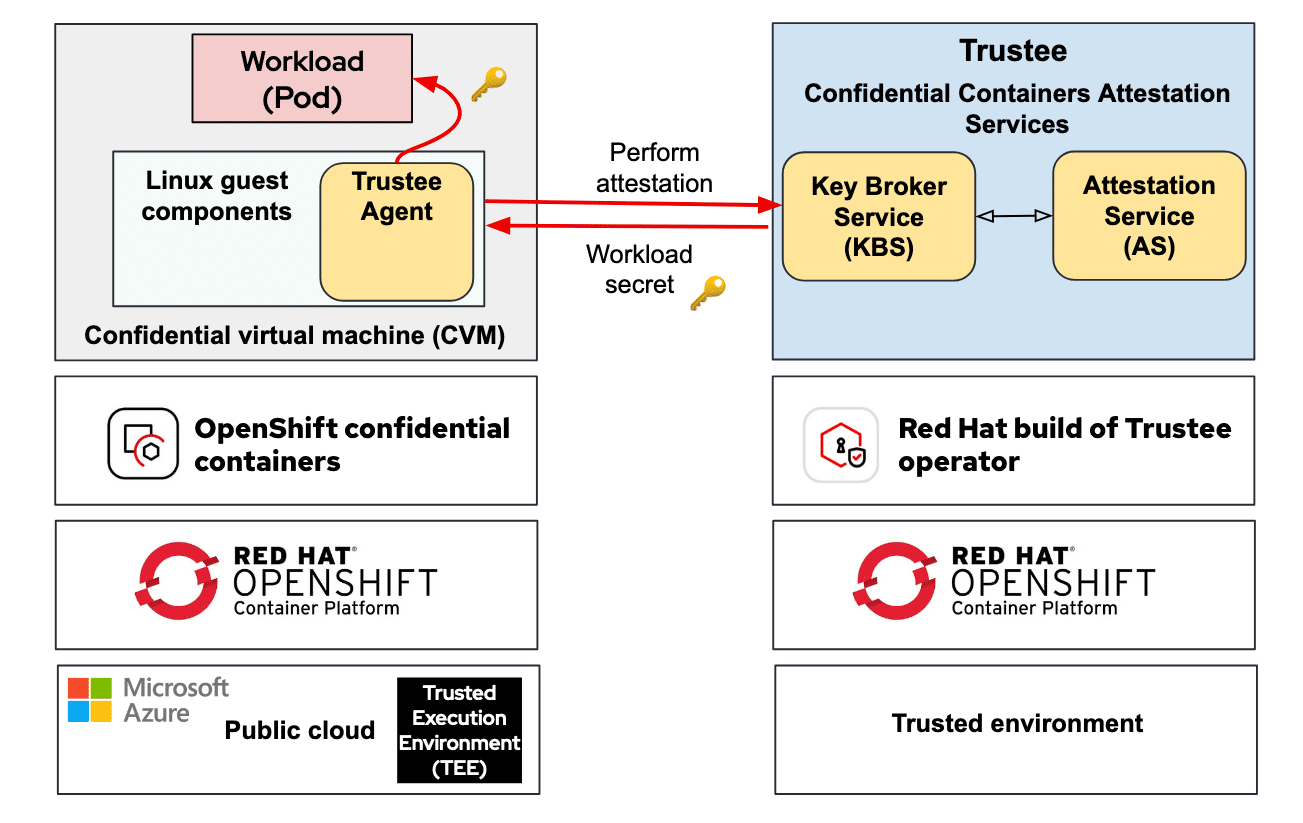
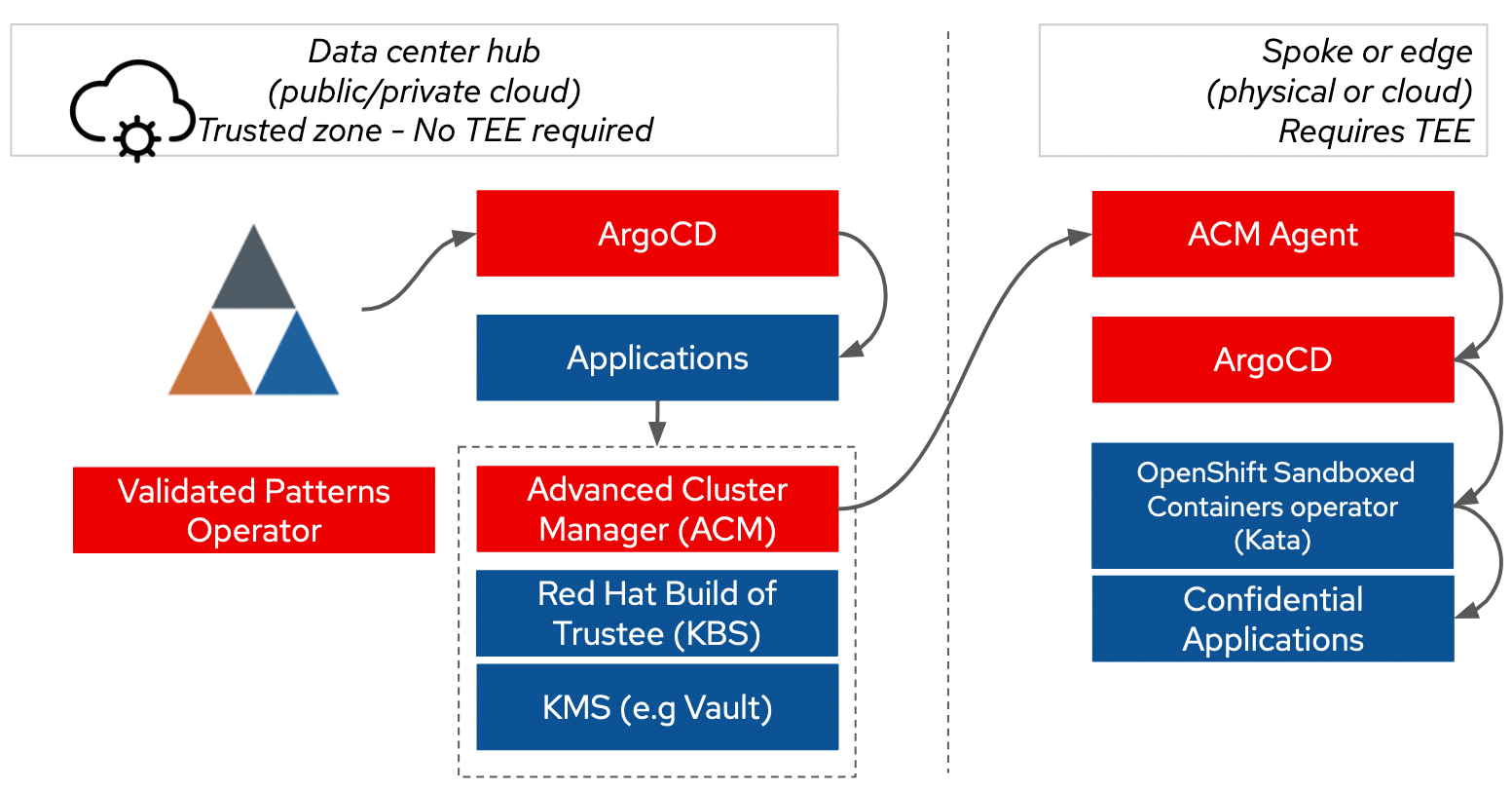
Confidential Containers Architecture
CoCo’s architecture is built around two key operators:
- OpenShift Confidential Containers Operator – Sets up the essential components that link pods with Confidential Virtual Machines (CVMs), leveraging hardware-based Trusted Execution Environments (TEEs).
- Remote Attestation Operator – The Trustee build deploys the Key Broker Service (KBS), responsible for secure key management and attestation.
Deployments are generally divided into two areas: a trusted zone where the Trustee operates, and an untrusted zone controlled by the sandbox container operator. These zones must be carefully configured based on hardware and cloud environments like Azure, requiring considerations such as region availability and chipset compatibility.
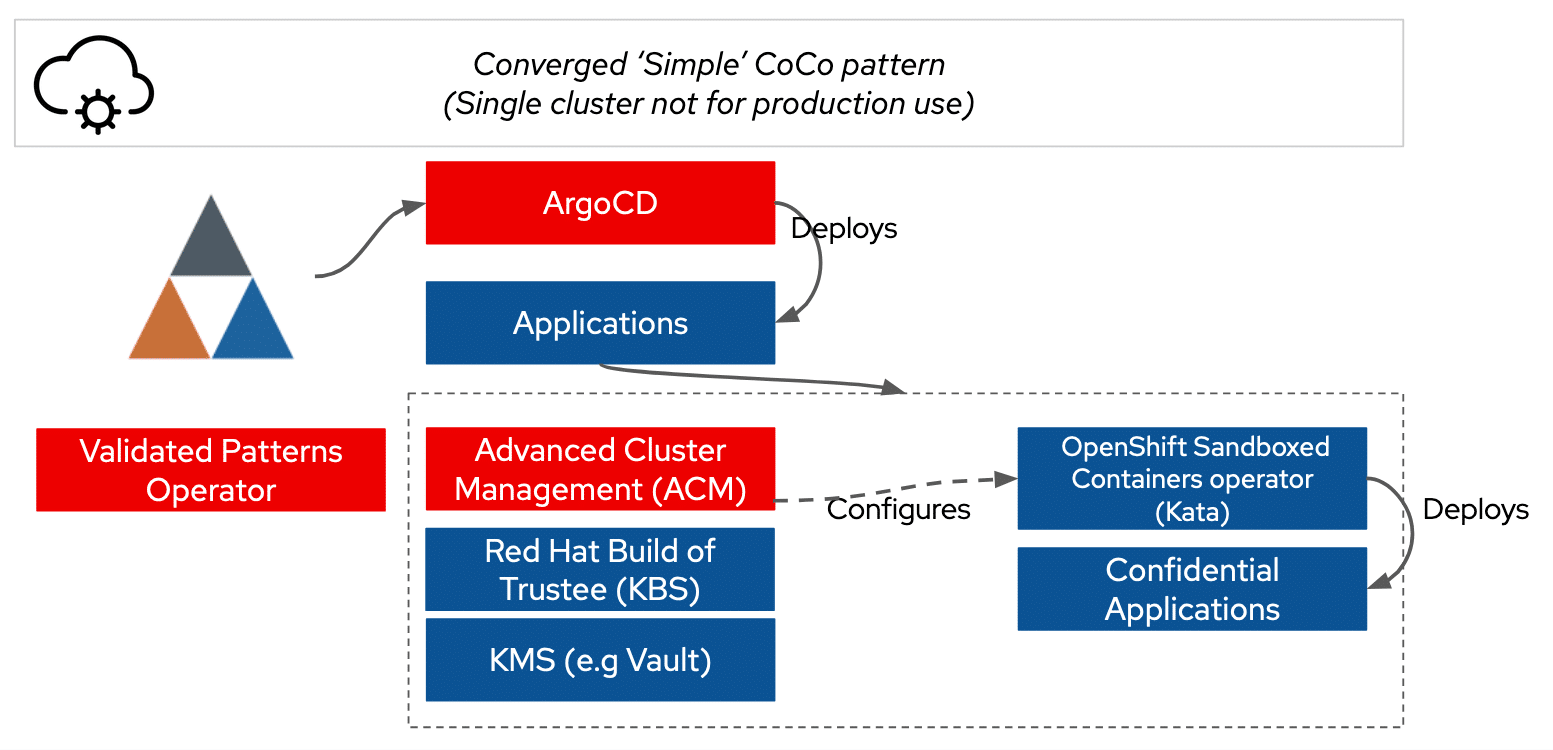
Introducing the Confidential Container Pattern
The validated pattern simplifies deployment by:
- Installing required operators and configuring certificates.
- Hiding cloud-specific complexities to simplify deployment with tools such as Red Hat Advanced Cluster Manager.
- Providing sample applications to explore CoCo’s capabilities.
Currently, this pattern supports deployment on Microsoft Azure with all components derived from a single pattern, and further expansions are in progress.
How It Works
Using Argo CD, the pattern operator automates deployments by orchestrating dependencies. Dynamic configuration challenges, such as securely passing information to the Key Broker Service, are addressed by leveraging metadata injection and advanced cluster management policies.
HashiCorp Vault is integrated to manage keys within the cluster, and secrets synchronization is handled using external secrets operators, ensuring secure and seamless operations.
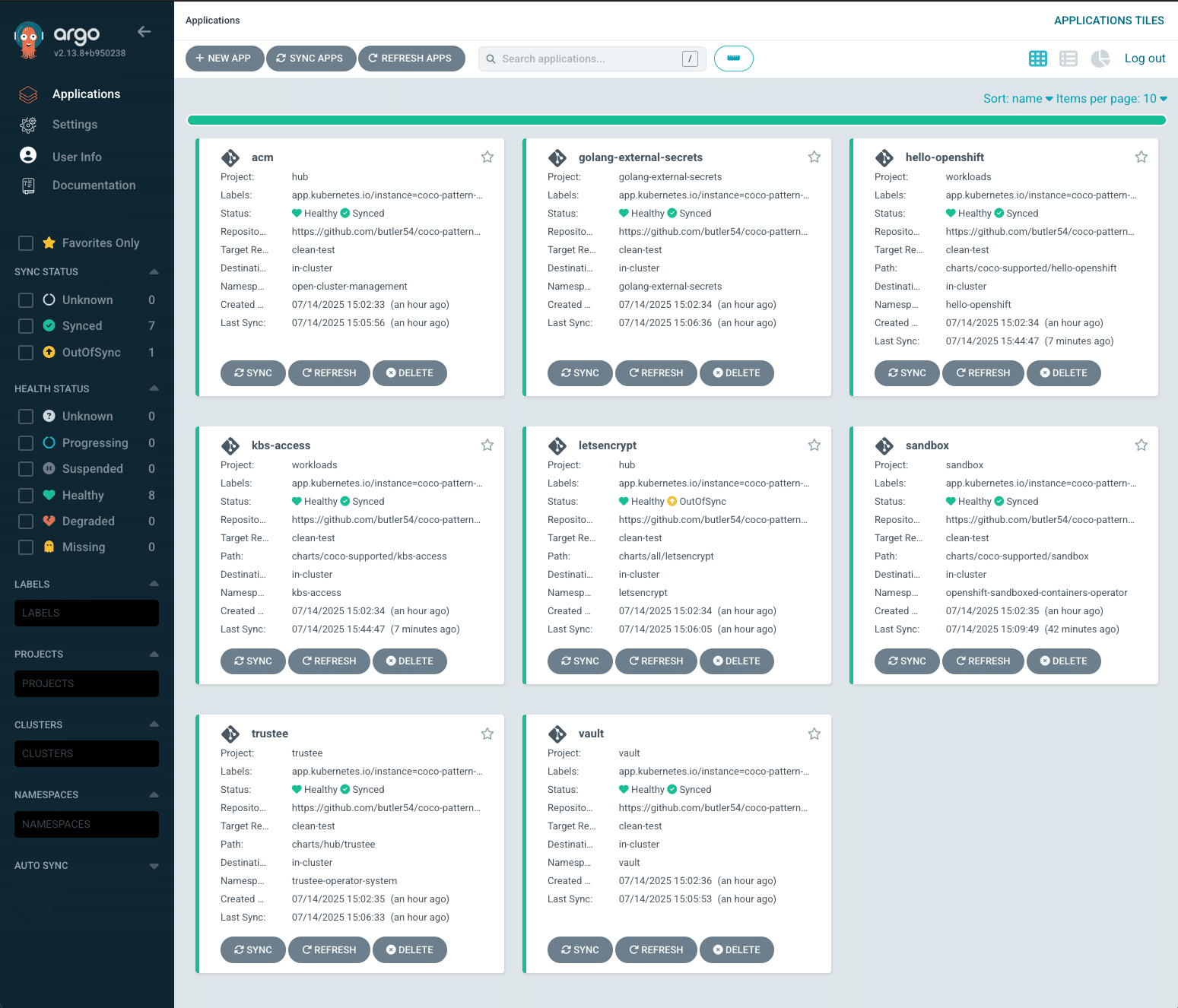
Installation Made Simple
With this approach, installation is reduced to a few straightforward steps:
- Create a Fork – Clone the pattern repository into your organization’s GitHub space.
- Generate Secrets – Run scripts to create necessary keys and credentials.
- Install the Pattern – Use OpenShift’s CLI to deploy everything with a single command.
Once deployed, users can explore sample applications like `hello-openshift` and `kbs-access` to learn how CoCo workloads function.
Security Considerations
While Confidential Containers enhance security, it’s essential to:
- Tailor attestation policies to your organization’s needs.
- Deploy the Trustee in a separate environment to reduce security risks.
By following these guidelines, you can achieve a deployment that is both secure and compliant.
Future Directions
Red Hat plans to expand the CoCo validated pattern by supporting:
- Multi-cluster architectures for large-scale deployments.
- Managed storage encryption and advanced secret management.
- Additional cloud and on-premise environments to ensure broader adoption.
Conclusion
The confidential container validated pattern offers a streamlined path for exploring and deploying CoCo solutions. By leveraging standardized architectures, GitOps workflows, and automated deployment processes, organizations can experiment, customize, and scale secure workloads confidently across hybrid and multi-cloud environments.