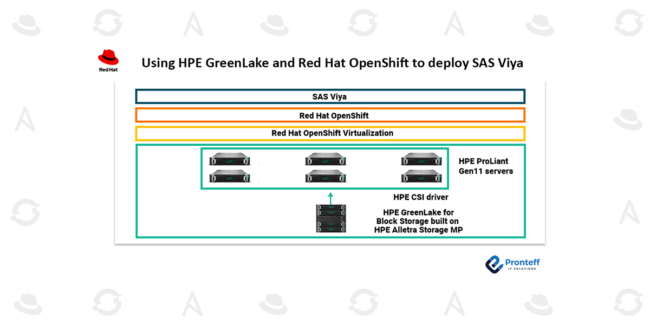
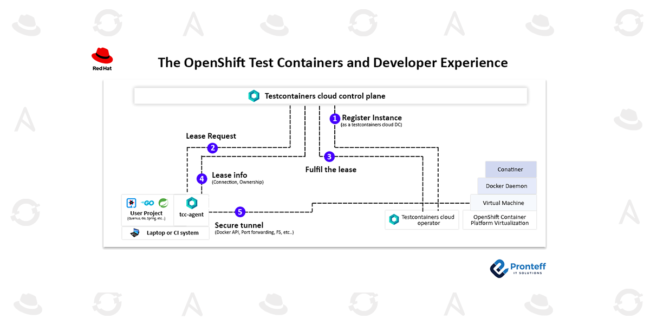
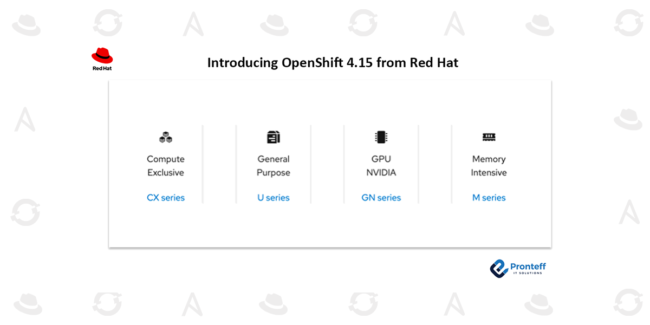
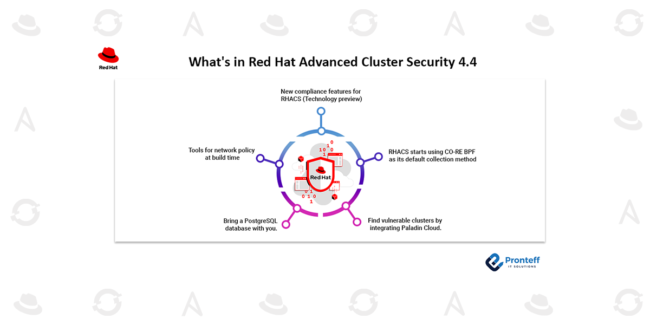
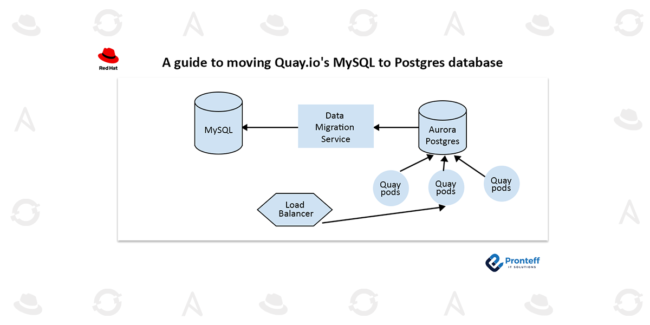
Using HPE GreenLake and Red Hat OpenShift to deploy SAS Viya
Using HPE GreenLake and Red Hat OpenShift to deploy SAS Viya Here in this blog, we will learn how to deploy SAS Viya using HPE Greenlake and Red Hat Open Shift. Based on a contemporary, containerized microservices-based architecture, SAS Viya is a high-performance AI and analytics platform that facilitates quick and flexible data-driven decision-making. SAS…