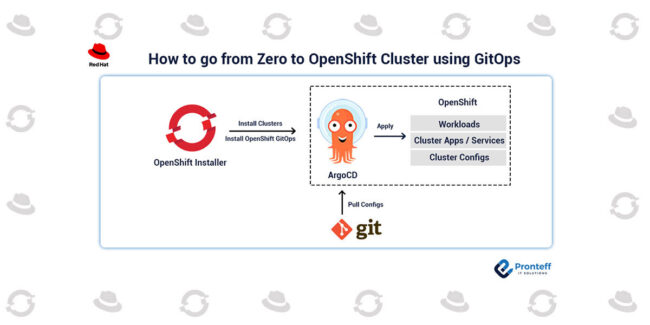
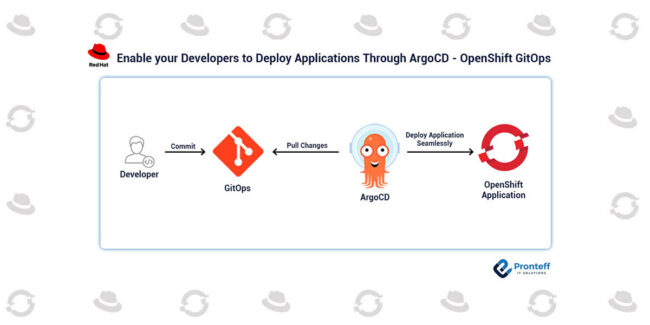
Red Hat Advanced Cluster Security, Q2 2022 Edition: What’s new
Red Hat Advanced Cluster Security, Q2 2022 Edition: What’s new In the second zone of 2022, Red Hat Advanced Cluster Security endured to create and decorate competencies designed to enhance protection programs, including delivering chain protection and zero-believe networking for Kubernetes. Our trendy updates, launched in 3.69 and 3.70, consist of enhancements to vulnerability management,…