Utilize Policy-based Governance with Red Hat Advanced Cluster Management for Kubernetes
Enterprise clients who undertake cloud are coping with the use of a couple of cloud providers, and dynamic cloud environments, and want to fulfill employer safety necessities and regulatory compliance necessities. Customers decide on open supply and now no longer have proprietary solutions. Hence, a technique that permits non-stop safety and audit readiness for open, hybrid multicloud is needed. Multicluster control calls for a centralized technique to perform to the employer and regulatory compliance standards. Our technique for accomplishing this intention is coverage-primarily based totally policy-based governance which makes use of regulations to symbolize first-class practices and automatic remediation of coverage violations whilst possible. This weblog collection makes a specialty of coverage-primarily based totally governance for multicluster control to gain safety and compliance in a multicloud environment.
First, let’s evaluate a few introductions approximately the governance structure and a few well-known concepts. Then, discover ways to write and use the distinct styles of policies. See a few examples of approximately distinct alternatives to reveal one’s policies.
Red Hat Advanced Cluster Management for Kubernetes allows cluster, software, and the safety lifecycle of hybrid and multicloud environments. Enterprises need to meet inner requirements for software program engineering, stable engineering, resiliency, safety, and regulatory compliance for workloads hosted on private, multi, and hybrid clouds. Teams that offer organization cloud platforms, in addition to software enterprise gadgets that run their enterprise programs on similar cloud platforms, can use Red Hat Advanced Cluster Management for Kubernetes governance functionality. Use the governance functionality to advantage visibility and force remediation for numerous safety and configuration elements to assist meet such organization requirements.
Governance architecture
Governance is an established manner of working an IT infrastructure primarily based totally on described policies, processes, and procedures. View the subsequent diagram of the governance architecture:
The governance structure consists of the subsequent components:
Dashboard: Provides a precis of your cloud governance and hazard details, which consist of coverage violations.
Policy UI, CLI, GitOps: Support coverage advent and deployment to diverse controlled clusters primarily based totally on attributes related to clusters, which includes a geographical region.
Policy save: Uses Kubernetes and many others to save guidelines as CustomResourceDefinition (CRD) objects.
Controls: Security and configuration controls are designed for diverse agency standards.
Policy consumers: Compare one or more policies at the controlled cluster to your specific control and produce Kubernetes activities if any are violated. There is the propagation of violations to the hub cluster.
When you observe the governance structure in your cluster, your cluster governance meets the subsequent functionalities:
- Extensible coverage framework that lets in introduction and distribution of regulations to controlled clusters from the hub cluster.
- Ability to combine more than one coverage language, inclusive of Open Policy Agent.
- Collection of coverage violation information from the hub cluster.
- Customization of regulations with the aid of using clients with the aid of using annotating compliance requirements, managing categories, and controls
- The policy dashboard is available for clients to customize their view and display coverage violations with the aid of using compliance requirements and managing categories.
Governance Lifecycle
View the subsequent diagram and an outline of the governance flow:
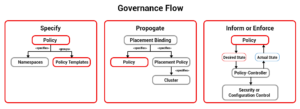
Let’s elaborate on the direction of the drift a little more:
- Initially, guidelines are created and propagated to controlled clusters with the use of the Red Hat Advanced Cluster Management for Kubernetes console, command line interface (CLI), or GITOPS.
Note: Any Kubernetes (K8S) item such as custom useful resource definitions (CRDs), may be represented as an item template in the specification phase of coverage. More than one item template CRD may be laid out in an unmarried coverage. When the coverage is deployed to controlled clusters, it may be enforced through both K8S, operators, or coverage controllers that technique the respective item template CRDs.
- Policy controllers are deployed on controlled clusters for numerous protection controls.
- Policy controllers periodically test specific guidelines in opposition to manipulating the kingdom and remediate the violation. When the controller is about to inform, a file of the violations is created. When the controller is about to put in force violations are remediated as specific withinside the coverage.
- The coverage popularity is propagated to the hub cluster from every controlled cluster.
- The hub cluster presentations coverage violations prepared through controlled clusters, guidelines, and additionally through compliance requirements and manipulate categories.
- Policies may be brought through 0.33 celebration to manipulate companies and customers without modifications to the Red Hat Advanced Cluster Management for Kubernetes coverage framework.
OPEN SOURCE COMMUNITY
Red Hat Advanced Cluster Management for Kubernetes coverage framework, coverage controllers, and guidelines are aside from the subsequent open supply project: open-cluster-management. You can use the open supply guidelines to create custom annotations in the coverage templates to specify one or extra compliance standard, manage class, and manage.
This open supply coverage framework may be used as the muse to broaden guidelines for digital machines, containers, middleware, applications, and hardware root of trust.
Security requirements and management classes
When you create a coverage, you may pick out a compliance standard, manage class, and manage. The following requirements are predefined: HIPAA, NIST, PCI or PCI-DSS, and FISMA.
You also can outline your very own standard, for instance, Common Criteria. For extra information, see Common Criteria.
A manage class represents the presence of precise necessities for one or extra controls, for instance, System and Information integrity. This class may suggest that this coverage includes an information switch protocol protective non-public information, as required with the aid of using the HIPAA and PCI requirements. You can create a brand new label for your manage classes with the aid of using including it immediately to the YAML file.
View the subsequent desk for an instance of coverage templates for NIST 800-fifty three specifications:
| NIST 800-53 Control family | Policy templates |
|---|---|
| Access control | Limit users with cluster-admin role, K8S role, K8S role binding |
| System and communications protection | Certificate management (expiration of certs) |
| System and information integrity | SCC, K8S pod security policy |
| Configuration | K8S resource limits, namespace, and pod |
Governance and risk
Let’s speak of special tracking alternatives for the Governance and chance dashboard.
You can view a top-level view of your cluster violations and coverage violations from the Governance and chance dashboard. The Policies web page shows a desk listing view of all the coverage violations. You can clear out the view of your cluster and coverage violations in your tabled listing.
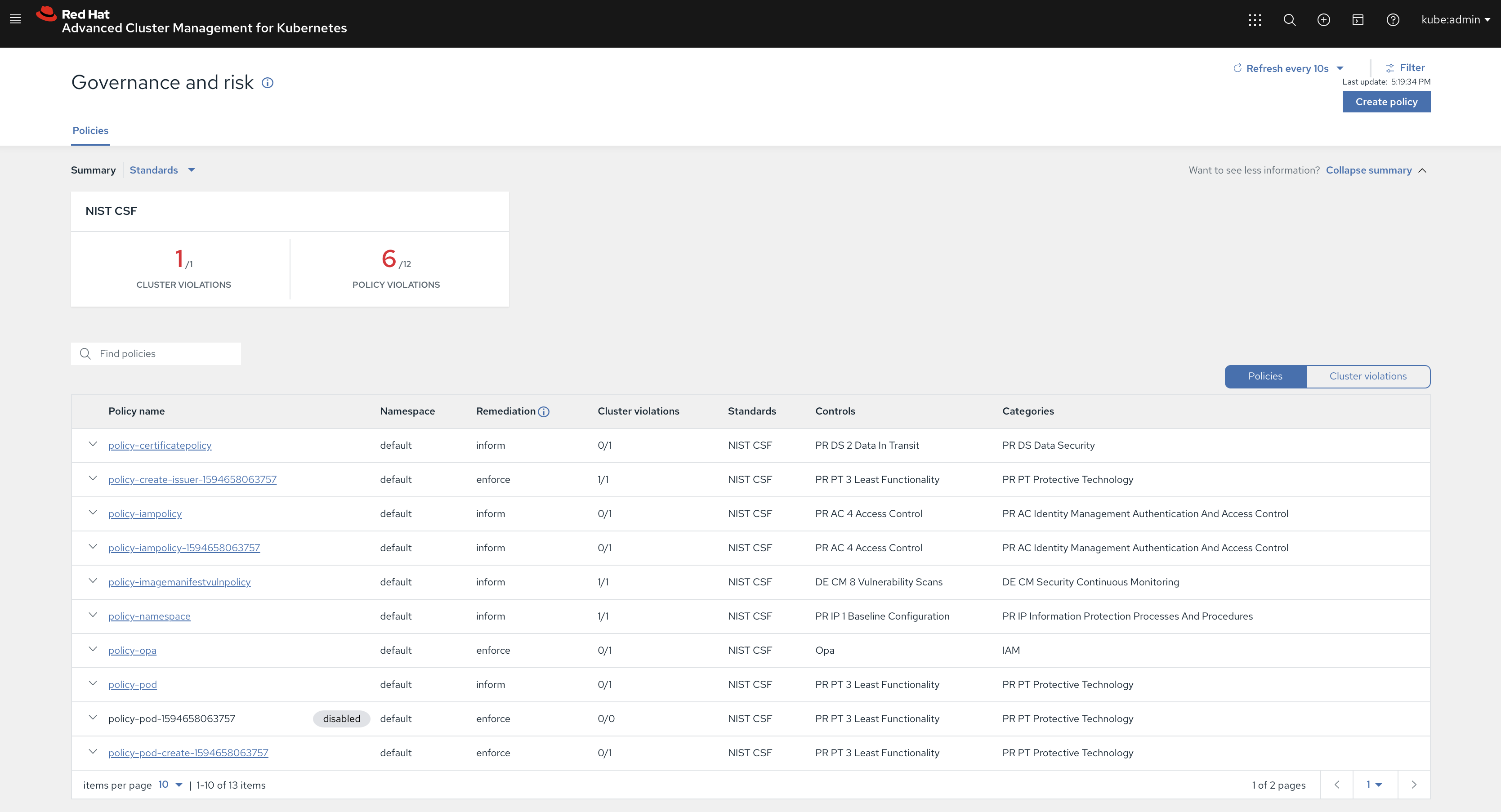
Select a particular coverage to view extra coverage information, consisting of placement coverage and location binding details, violations, and the YAML file. Policy violations are stated to the Red Hat Advanced Cluster Management for the Kubernetes hub cluster via way of means of the coverage controllers.
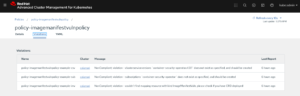
You also can create custom policies. View the subsequent photograph of a custom coverage this is incorporated with OPA:
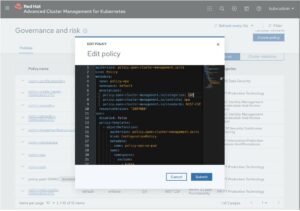
To study extra approximately developing custom coverage controller, see Creating a custom coverage controller withinside the product documentation.
Conclusion
Red Hat Advanced Cluster Management for Kubernetes governance affords an extensible framework for firms to introduce their very own safety and configuration guidelines. By writing a custom coverage controller, firms can without problems combine current organization safety and configuration controls with Red Hat Advanced Cluster Management governance. Enterprises also can take benefit of the Governance and danger dashboard to create and control each out-of-field guidelines and custom guidelines, screen the coverage compliance status, and take addition remediation actions








