Security Driver Operator for Red Hat OpenShift Secrets Store
In this blog, we will learn how the Security Driver operates for Red Hat OpenShift Secrets Store.
Introduction
In Kubernetes and OpenShift, managing secrets (passwords, API tokens, certificates, keys) securely is a critical challenge. By default, Kubernetes stores secrets in etcd, which, even when encrypted at rest, introduces security risks if not handled properly.
To address this, Red Hat introduced the Secrets Store CSI Driver Operator in OpenShift 4.18/4.19. This feature empowers clusters to fetch and mount secrets dynamically from external secret managers such as:
- HashiCorp Vault
- AWS Secrets Manager
- Azure Key Vault
- Google Cloud Secret Manager
Instead of persisting secrets in etcd, they are mounted ephemerally at runtime, reducing exposure and strengthening compliance.
Why is it needed?
Traditional Kubernetes secret handling has challenges:
- Secrets are stored in etcd, creating risks if etcd backups are not encrypted.
- Rotation of secrets is not automatic – manual updates are needed.
- Centralized enterprise secret managers (Vault, AWS, Azure) were not tightly integrated.
The Secrets Store CSI Driver Operator solves these problems by:
- Avoiding storage in etcd (secrets live only in memory).
- Dynamic retrieval from trusted external managers.
- Automated rotation – when secrets change in the external manager, the pod automatically receives updates.
- Centralized compliance – security policies remain managed in the enterprise vault.
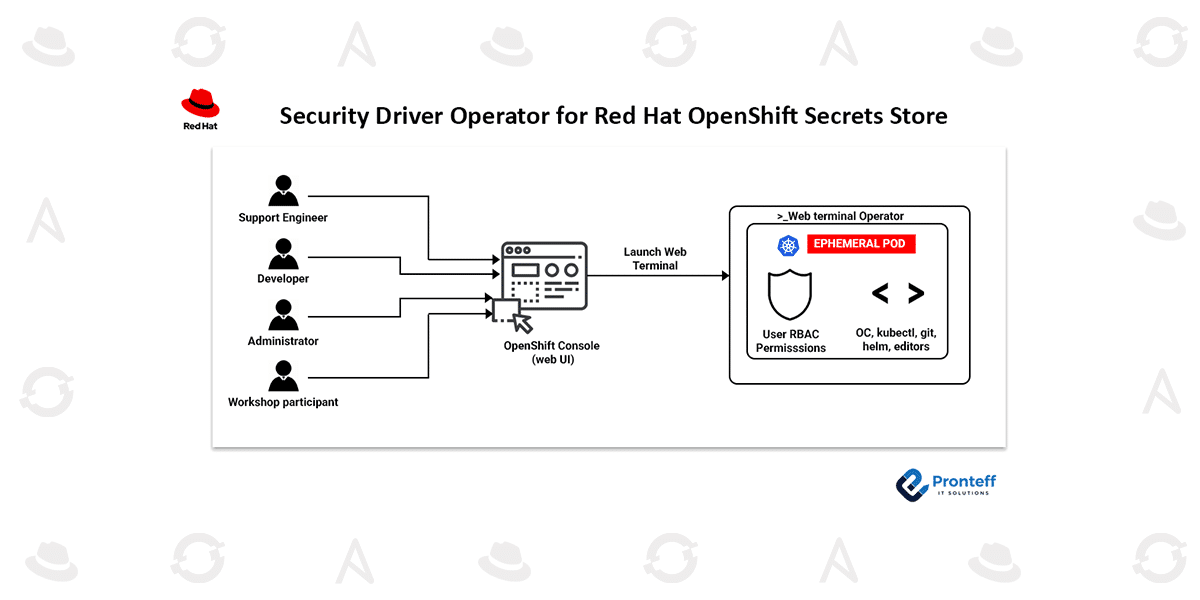
How It Works (Architecture)
Flow:
- A developer deploys a pod that needs a secret (e.g., database password).
- The pod mounts a volume using the Secrets Store CSI Driver.
- The driver fetches the secret from the configured external secret manager (Vault, AWS, Azure, etc.).
- The secret is mounted into the pod ephemerally (not persisted in etcd).
- Optional: The secret can also sync into a Kubernetes Secret object if needed for legacy apps.
Key Features
- Operator-managed lifecycle → Installation, upgrades, and configuration are handled natively through OpenShift OperatorHub.
- Ephemeral mounting → Secrets are injected into pods only at runtime.
- Sync with Kubernetes Secrets (Optional) → For workloads that still rely on Kubernetes secrets.
- Works with Multiple Providers → Vault, AWS, Azure, GCP.
- Secret Rotation → Secrets rotate automatically without manual redeployment.
Customer Benefits
- Enhanced Security – secrets don’t sit in etcd; they remain in external managers.
- Operational Efficiency – no need to manually update secrets across clusters.
- Compliance Ready – meets regulatory requirements for secret storage.
- Dynamic Rotation – applications pick up new credentials automatically.
- Hybrid-Cloud Friendly – works with multiple public cloud secret managers.
Real-World Use Cases
- Banking & Finance: Store API keys, tokens, and encryption keys securely in Vault or cloud KMS.
- Healthcare: Manage sensitive PHI credentials dynamically while ensuring HIPAA compliance.
- Multi-Cloud Deployments: Use different cloud providers’ secret managers seamlessly from OpenShift.
- DevSecOps: Automate credential injection into CI/CD pipelines without exposing secrets in code.
Conclusion
The Secrets Store CSI Driver Operator marks a major leap in cloud-native security for OpenShift. By eliminating the reliance on etcd for secret storage, it ensures sensitive data is managed securely and dynamically, directly from enterprise-grade secret managers.
For organizations adopting hybrid and multi-cloud strategies, this operator is not just a feature—it’s a security best practice that simplifies secret lifecycle management, improves compliance, and reduces operational overhead.
With OpenShift 4.19, enterprises gain a trusted, flexible, and secure way to manage secrets natively within their clusters.