Hybrid Confidential Computing with OpenShift 1.11 and Trustee 1.0
In this blog, we will learn about hybrid confidential computing with OpenShift 1.11 and Trustee 1.0.
Red Hat Advances the Next Phase of Confidential Computing
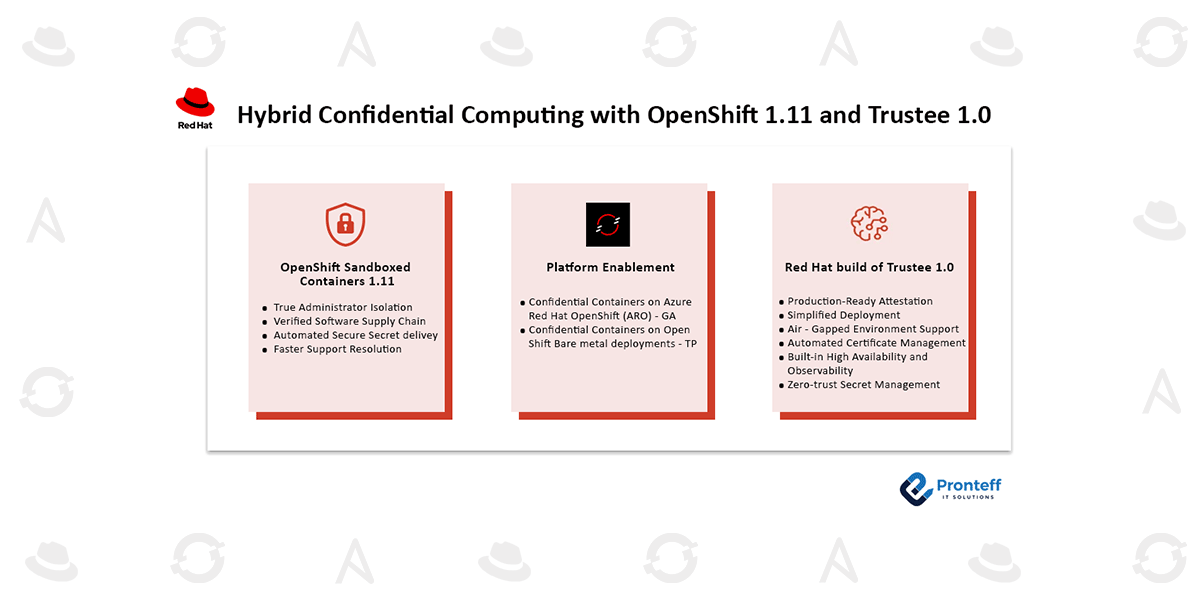
Red Hat is advancing its confidential computing strategy with the release of OpenShift sandboxed containers 1.11 and the Red Hat build of Trustee 1.0. Together, these releases introduce enterprise-ready confidential containers for Azure Red Hat OpenShift and provide early access support for bare metal environments using Intel TDX and AMD SEV-SNP hardware.
Organizations can now safeguard highly sensitive workloads using hardware-enforced isolation, encrypted memory, and cryptographic attestation, consistently across cloud and on-premises platforms.
What’s New in This Release
OpenShift Sandboxed Containers 1.11: Designed for Secure Operations
OpenShift sandboxed containers 1.11 strengthens isolation boundaries while improving day-to-day usability for security-focused teams.
Isolation is enabled by default
Confidential containers now run with a restrictive agent policy turned on automatically. This prevents administrative access from the host—such as interactive command execution—ensuring workloads remain isolated even from cluster operators. A controlled debug option can be enabled explicitly for development use cases.
Stronger supply chain assurance
Expanded support for signed container images helps ensure only verified and trusted workloads are deployed, reinforcing end-to-end software integrity.
Attestation-driven secret access
Secrets are released only after a workload’s integrity has been verified. Using Trustee, sensitive information such as credentials or cryptographic keys is delivered only to containers that successfully pass hardware-backed attestation checks.
Easier troubleshooting
Enhanced must-gather capabilities now automatically include attestation service logs, simplifying diagnostics and reducing time to resolution during support engagements.
Red Hat Build of Trustee 1.0: Simplified Attestation for Enterprise Environments
The Red Hat build of Trustee 1.0 provides production-grade remote attestation services and acts as the trust anchor for confidential workloads. A newly introduced Trustee configuration custom resource dramatically reduces setup effort, replacing complex manual configuration with a concise, declarative model.
Key capabilities include:
Air-gapped and disconnected deployments
Trustee fully supports isolated environments, including automated caching of AMD VCEK certificates for SEV-SNP systems. Multiple processor generations—such as Milan, Genoa, and Turin—can be supported simultaneously, addressing strict compliance and regulatory requirements.
Operational readiness for production
Native integration with cert-manager automates certificate lifecycle management for HTTPS endpoints and attestation tokens. High availability is achieved through Kubernetes-native scaling and distributed configuration storage.
Visibility and developer tooling
Built-in Prometheus metrics provide insight into attestation health and performance, while the Trustee CLI enables local testing, development workflows, and advanced deployment scenarios.
By ensuring secrets are never exposed unless a workload is cryptographically verified, Trustee enforces a zero-trust security model where sensitive data remains protected from administrators and infrastructure operators alike.
Confidential Containers Reach General Availability on Azure Red Hat OpenShift
Azure Red Hat OpenShift is jointly operated by Red Hat and Microsoft, delivering a fully managed OpenShift experience on Azure. With this release, confidential containers are now generally available, offering customers a managed path to protect data while it is actively being processed.
By leveraging Azure’s trusted execution environments, workloads are isolated from host systems, cloud operators, and neighboring tenants—providing strong assurances for regulated and security-sensitive applications.
This general availability milestone is backed by extensive validation and optimization, including:
- Reduced startup latency through optimized virtual machine initialization
- Improved cloud integration, enabling reuse of pre-built VM images for peer pods
- Production-proven stability, with continuous validation across Azure environments
Bringing Confidential Containers to Bare Metal (Technology Preview)
Confidential computing is no longer limited to the cloud. A new technology preview allows confidential containers to run directly on OpenShift 4.20 and later on bare metal systems equipped with AMD SEV-SNP, Intel TDX, or IBM LinuxONE hardware.
This preview introduces automated workflows that simplify deployment:
- Automatic detection of TEE-capable nodes
- On-demand creation of confidential runtime classes
- Host configuration managed through MachineConfigs
These capabilities significantly lower the barrier to entry, allowing teams to deploy their first confidential workload on physical infrastructure with minimal effort.
Proven Value in Real Environments
Confidential containers are already delivering measurable impact. DBS Bank successfully modernized its digital asset custody platform using OpenShift with confidential containers—an industry-first deployment. The initiative improved security posture, reduced operational risk, and enabled faster innovation in a highly regulated environment.
The deployment was recognized with the AI & Emerging Tech award at the Red Hat APAC Innovation Awards 2025, demonstrating the real-world viability of confidential computing for mission-critical financial services.
Looking Ahead
Red Hat’s roadmap for confidential computing continues to expand:
- Broader bare metal enablement for performance-critical workloads
- Confidential AI support, including secure GPU-based workloads
- Expanded cloud coverage across additional OpenShift platforms
- Continued simplification of deployment and operations
The focus remains on delivering consistent, hardware-backed security wherever OpenShift runs.
Get Started Today
The most sensitive workloads require protection that extends beyond traditional isolation models. Confidential containers on OpenShift keep data encrypted and protected—even from infrastructure administrators.
You can begin using confidential containers today through the Red Hat Hybrid Cloud Console and start securing critical applications in minutes.