OpenShift Confidential Containers Now on Microsoft Azure
In this blog, we will learn how OpenShift Confidential Containers Work on Microsoft Azure.
Red Hat has officially announced the general availability of OpenShift Confidential Containers (CoCo) on Microsoft Azure, empowering organizations to run containerized applications with reinforced security. This launch gives enterprises the confidence to handle sensitive workloads in confidential environments where information stays protected even while being processed. By using hardware-based Trusted Execution Environments (TEEs), CoCo enhances both privacy and data integrity—marking a significant step in bringing confidential computing to Azure.
Bringing Confidential Containers to Azure
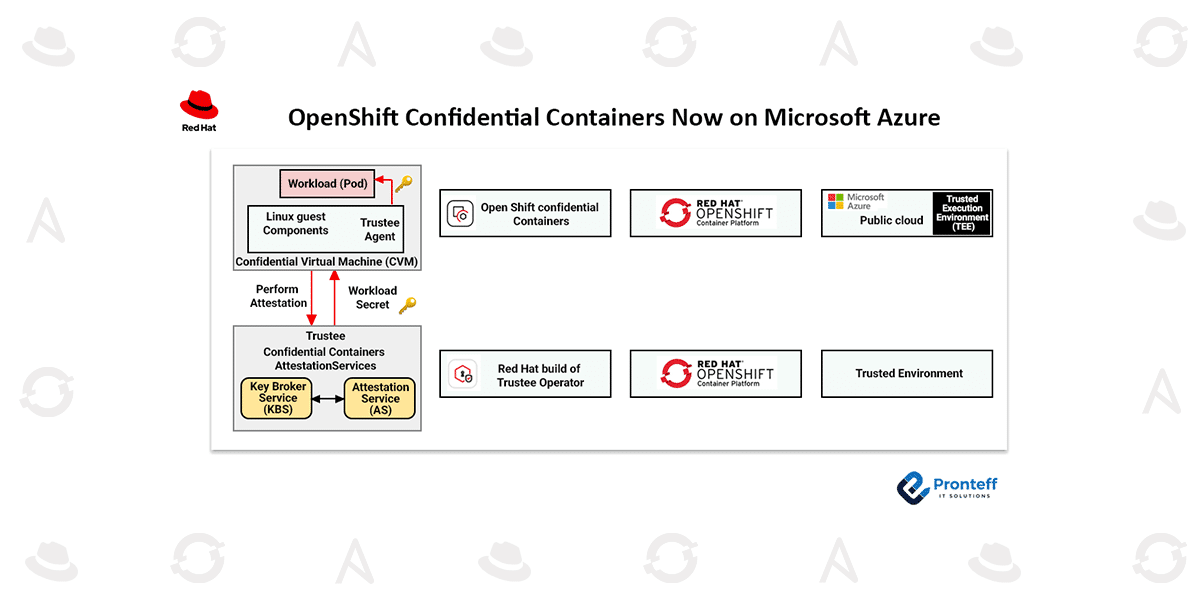
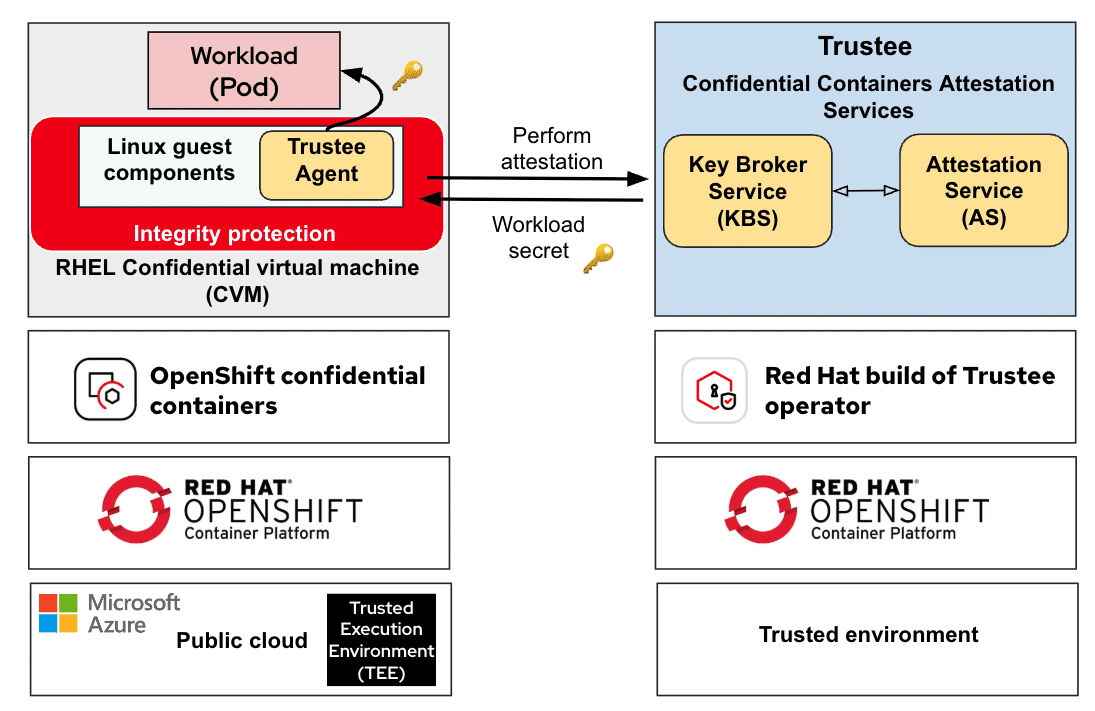
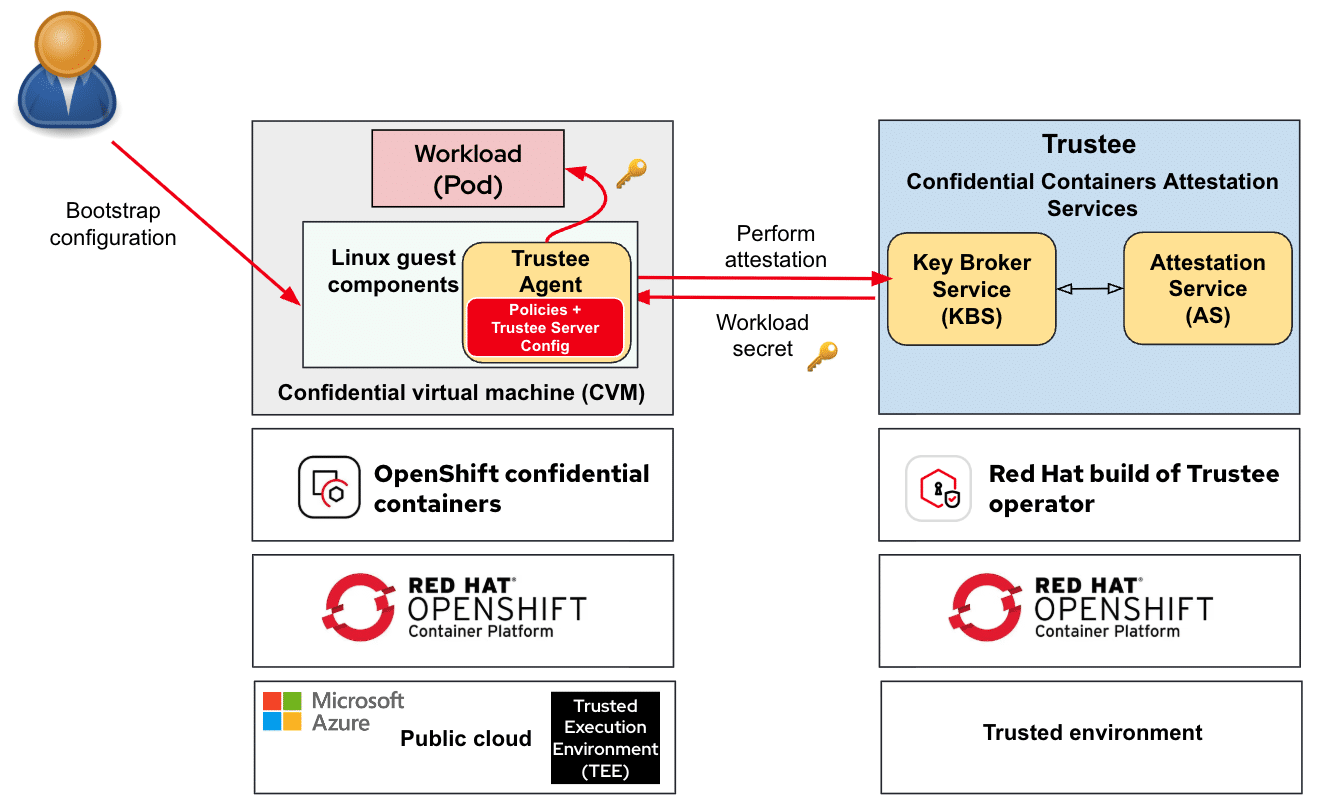
OpenShift Confidential Containers bring the advantages of confidential computing into the cloud-native landscape. Central to this approach is the Trusted Execution Environment (TEE)—a hardware-enabled secure enclave that keeps workloads isolated and shielded from unauthorized access. On Microsoft Azure, this is implemented through Confidential Virtual Machines (CVMs), which form the underlying foundation of CoCo.
Within these CVMs, CoCo launches pods that become confidential pods, ensuring container workloads operate with an additional layer of protection.
A crucial aspect of this process is attestation—verifying the integrity of the TEE before execution. This ensures that data and code only run in environments proven to be secure. In CoCo, attestation is handled by the Trustee project, which validates the environment and securely delivers secrets once trust has been established.
Architecture Overview
The CoCo framework is built on two main components:
Confidential Virtual Machines (CVMs): Secure, isolated virtual machines that act as the foundation for running confidential pods.
Trustee for Attestation: Validates TEEs and releases secrets only to verified environments.
For a deeper dive, see resources such as Exploring the OpenShift Confidential Containers solution and Use cases and ecosystem for OpenShift Confidential Containers.
Strengthened Integrity for CVM Images
In this update, CoCo pod VM images gain integrity verification through dm-verity, a Linux kernel mechanism that ensures block devices remain consistent and unaltered.
- After the CVM image is built, its root disk is locked in read-only mode.
- Any tampering attempts are detected during startup, preventing execution in untrusted states.
- This safeguard is essential since images often travel across less-trusted stages, like downloads, registries, or deployments.
With these protections, CoCo ensures that the base OS and the Trustee agent within the CVM remain free from modification.
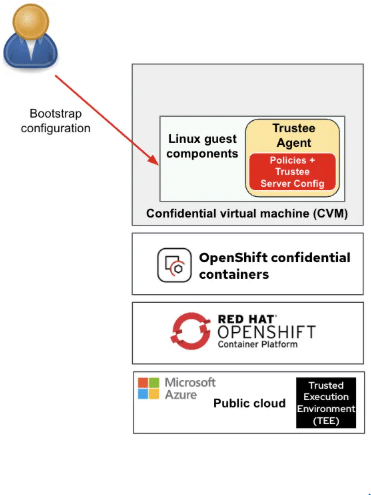
Dynamic Bootstrap for Pods
Previously, CoCo supported only static configurations. The latest update introduces dynamic bootstrap configuration through measured initdata.
This capability enables:
Per-pod access rules: Define what actions a pod can take and which images it can run.
Multiple attestation servers: Assign separate Trustee servers to handle verification for different tenants or individual workloads.
Tenant-specific trust policies: Apply stricter requirements, such as mandating signed container images.
Bootstrap data is injected before the pod is created, ensuring that security rules and Trustee details are enforced from the very beginning of the workload lifecycle.
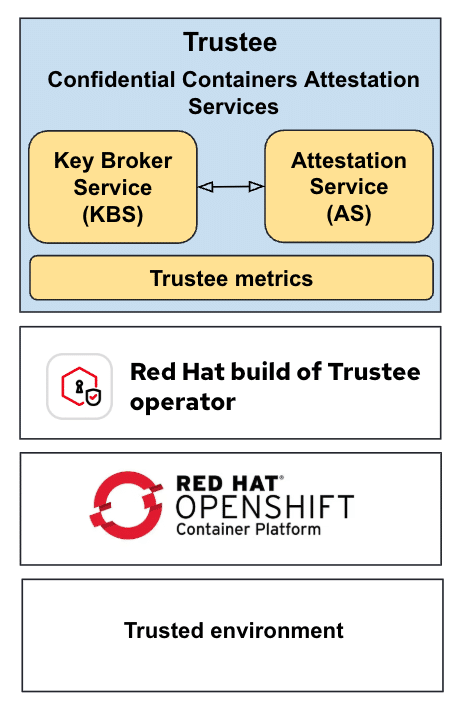
Monitoring with Trustee Metrics
Observability has been improved with Prometheus-powered monitoring for the Trustee attestation service. Available metrics include:
API performance metrics: Tracks the number of requests, latency, and data sizes handled by Key Broker Service (KBS) APIs.
Resource-level tracking: Secret reads and writes recorded with per-resource detail.
Dedicated metrics endpoint: A Prometheus scrape target for data collection and cleanup.
These enhancements help operators monitor performance, track usage, and configure alerts for confidential container workloads.
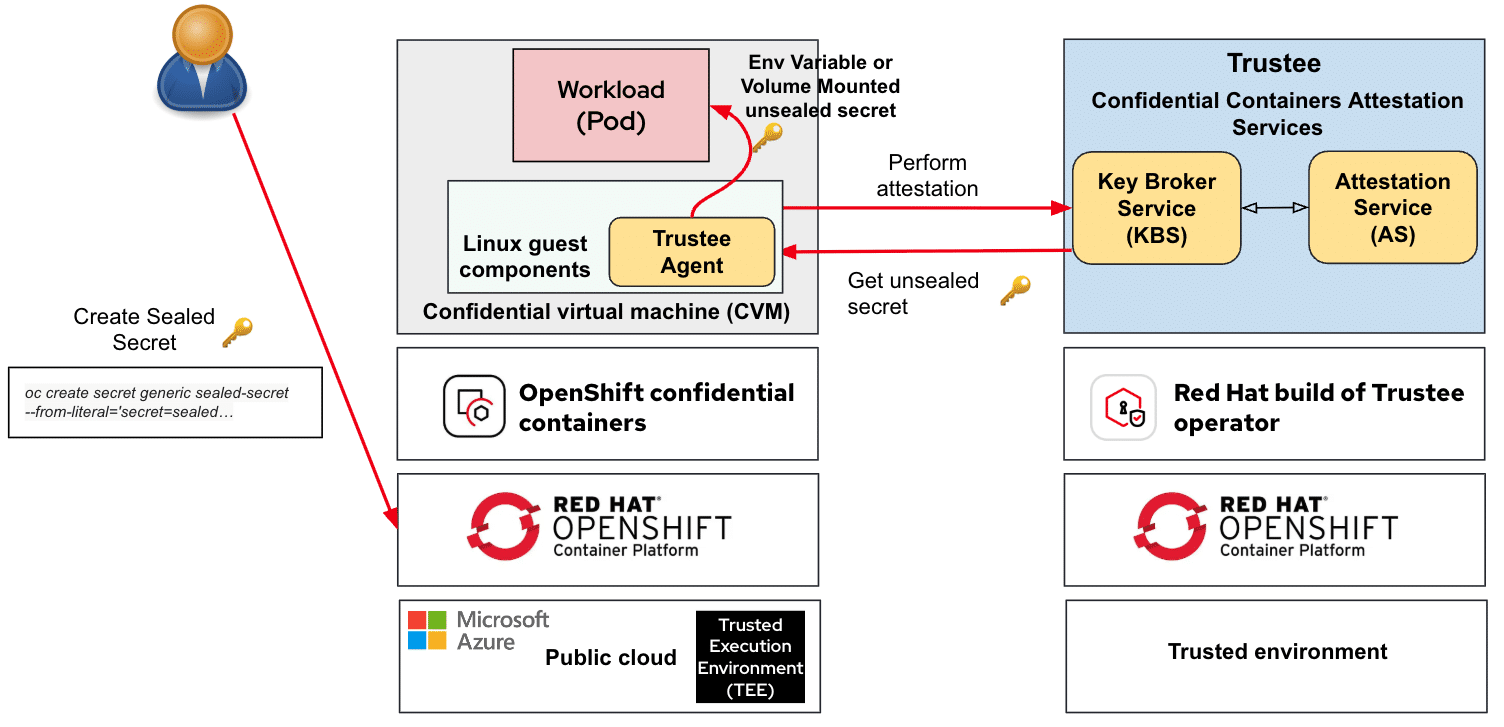
Sealed Secrets for Confidential Workloads
Support for sealed secrets is now available, providing a way to keep sensitive data protected in the control plane while making it usable only inside a trusted TEE.
Process flow:
- A sealed secret is generated that references the original secret stored in Trustee.
- This sealed secret is attached to the pod specification like any OpenShift secret.
- Once the environment is validated through attestation, the Trustee agent retrieves the secret and injects it into the pod (as an environment variable or via a volume mount).
This guarantees that confidential data is only exposed once workloads have been validated and are operating in a trusted environment.
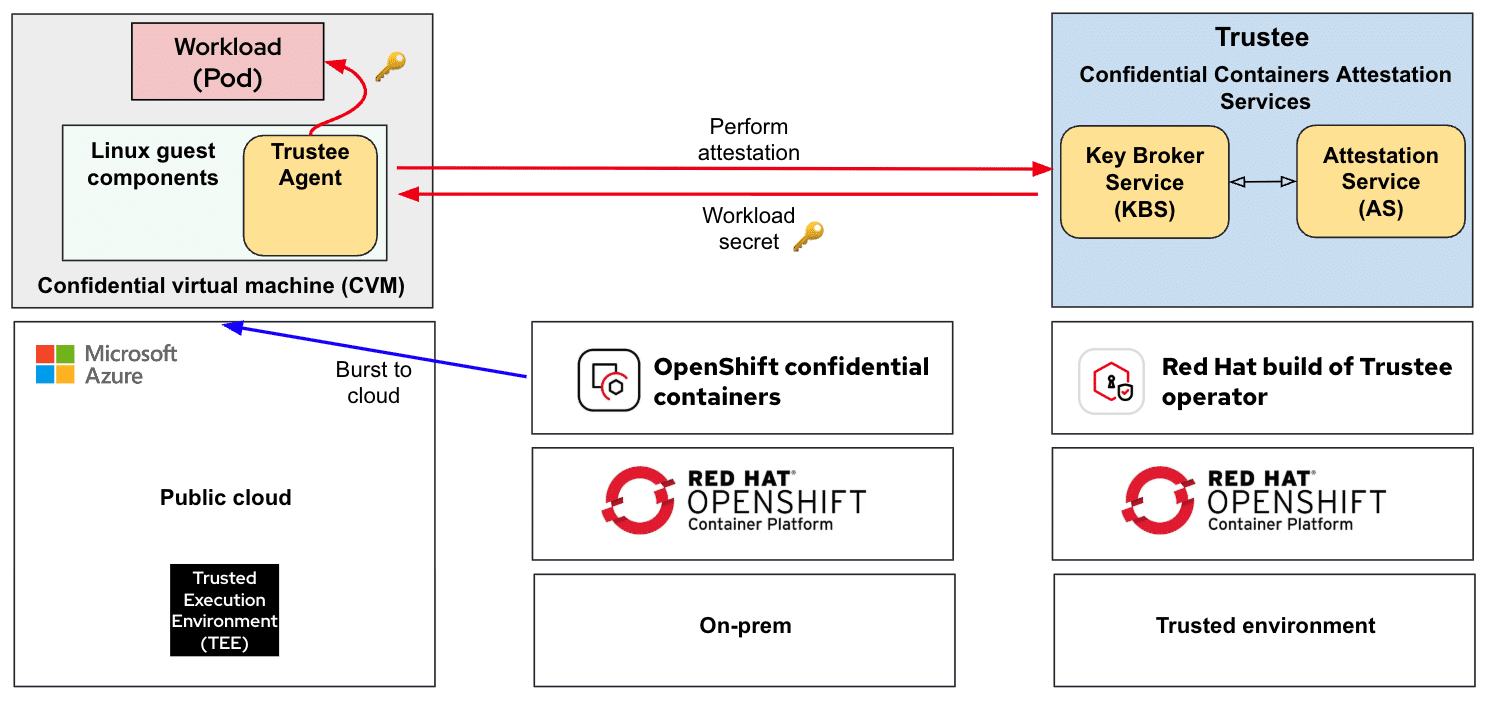
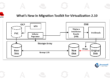
Hybrid Expansion: Secure Cloud Bursting
CoCo now enables secure cloud bursting from on-premises OpenShift clusters to Azure—without requiring a full OpenShift deployment in the cloud.
- The CoCo operator runs on an existing on-premises OpenShift cluster.
- Workloads can be burst into Azure by launching pods inside CVMs.
- Attestation continues to be performed by the same trusted Trustee server.
- From the user’s perspective, the workloads appear as if they are still running in the on-prem cluster.
This approach allows enterprises to scale into Azure while retaining centralized trust management. Future updates will broaden this model to fully on-premises environments, giving organizations the flexibility to balance local and cloud resources.
Roadmap: What’s Ahead for CoCo
The evolution of OpenShift Confidential Containers will expand support across more platforms and deployment models, including bare metal, additional cloud providers, and managed services. Key future enhancements include:
- Encrypted container image support
- Confidential GPU processing
- New layers of workload protection
These planned improvements aim to make confidential computing more flexible and applicable across diverse enterprise scenarios.