How Do EDB and Red Hat Enable Resilient Automation?
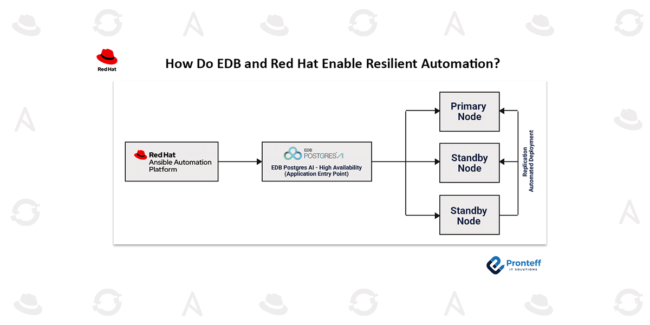
How Do EDB and Red Hat Enable Resilient Automation? In this blog, we will learn how EDB & RedHat enable Resilient Automation. In today’s fast-moving digital landscape, IT environments must consistently deliver high performance and reliability to keep business operations running without disruption. Centralized automation solutions like Red Hat Ansible Automation Platform play a vital…