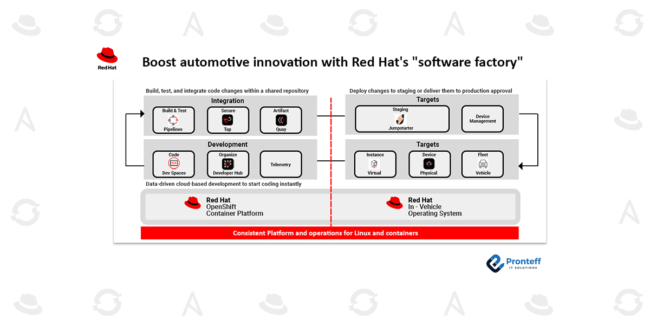
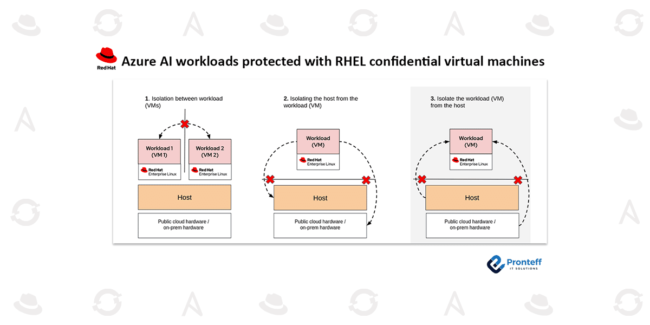
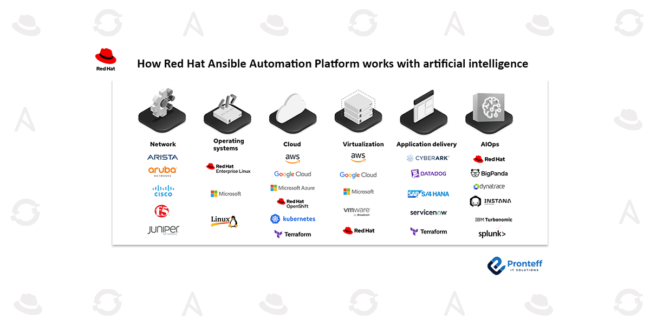
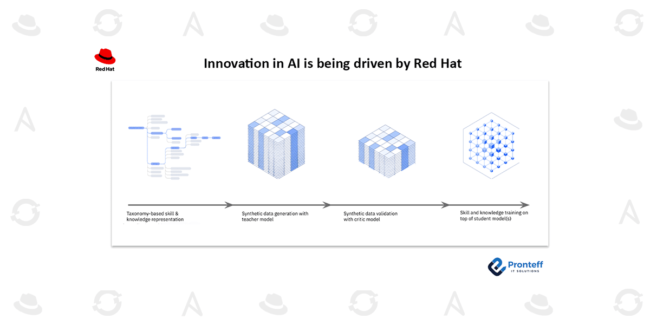
Disaster Recovery Strategies for Stateful Virtual Machines on OpenShift
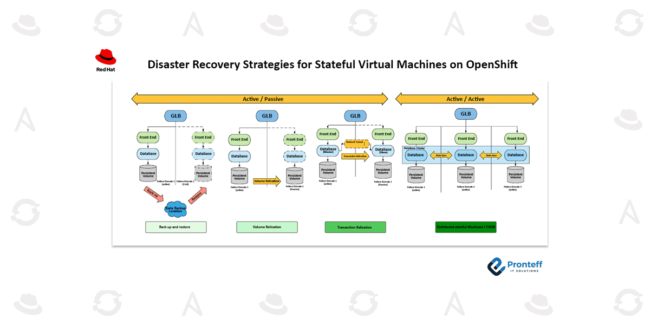
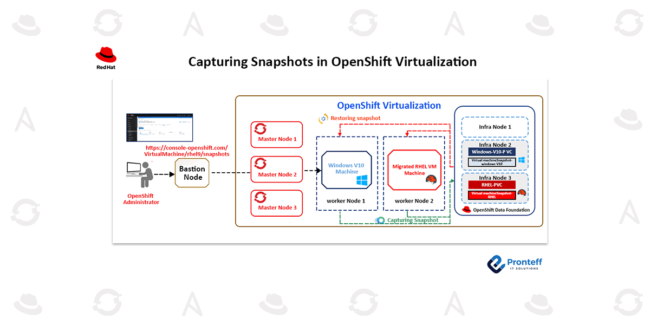
Disaster Recovery Strategies for Stateful Virtual Machines on OpenShift In this blog, we will learn about disaster recovery strategies for stateful virtual machines on OpenShift. As enterprises increasingly migrate critical workloads to Kubernetes platforms, ensuring robust disaster recovery (DR) for stateful virtual machines (VMs) has become a vital aspect of business continuity planning. Unlike stateless…