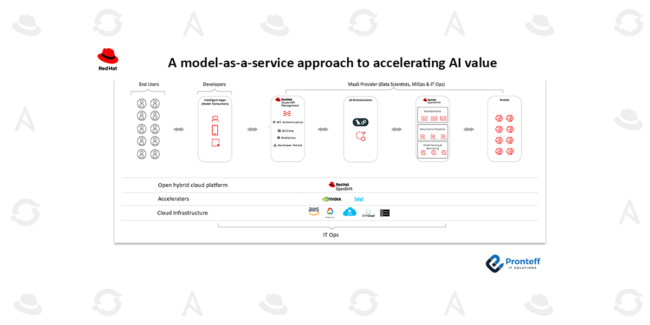
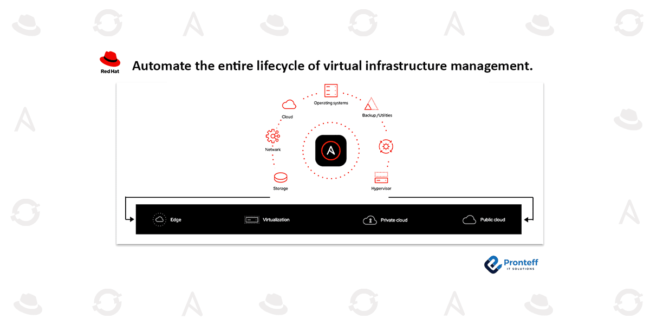
Innovation and growth through Red Hat Enterprise Linux
Innovation and growth through Red Hat Enterprise Linux In this blog, we will learn about Innovation and growth through Red Hat Enterprise Linux. IT Teams Face Increasing Demands In today’s fast-evolving digital landscape, IT teams are under growing pressure to effectively manage Linux-based operating systems (OS) while supporting complex workloads such as artificial intelligence and…