IBM MQ SSL connectivity using PKCS12 keystore
In this blog, we will learn about the IBM MQ SSL connectivity using the PKCS12 keystore.
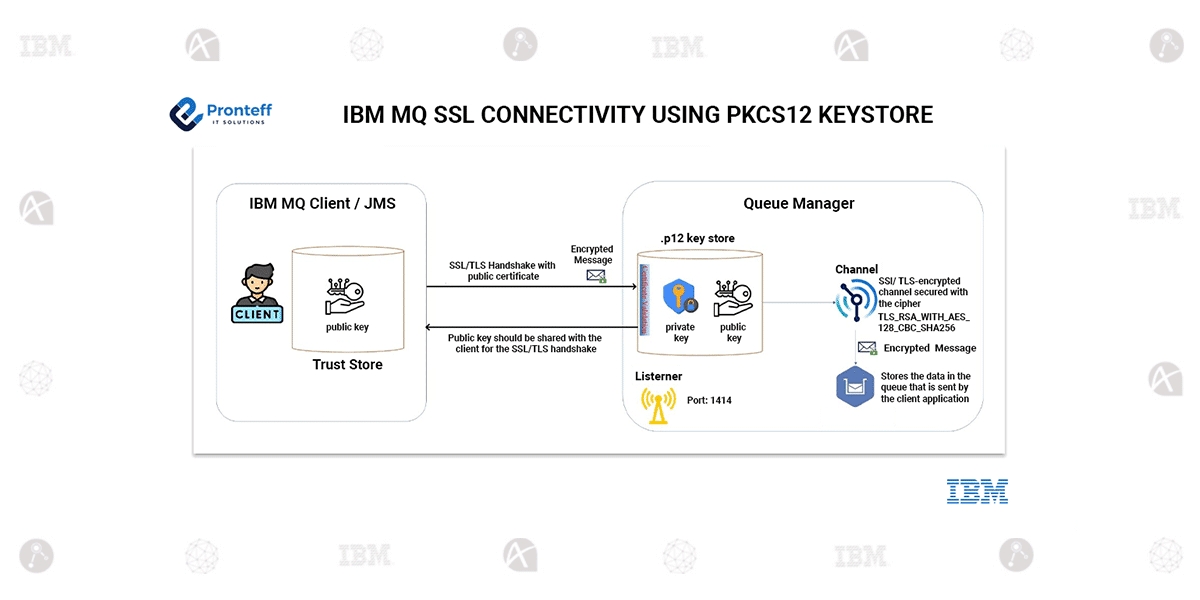
IBM MQ SSL connectivity using PKCS12 keystore Secure Management of Cryptographic Data in IBM MQ
What is PKCS12?
PKCS12 is a secure file format used to store cryptographic data, including private keys and certificates. It simplifies security management by bundling all necessary credentials into a single file.
Why is PKCS12 Important?
Standardized & Compatible – Works across various platforms and software.
Secure – Supports encryption to protect sensitive information.
Simplifies Management – Reduces complexity in handling security credentials.
Common Use Cases
Secure Authentication – Used for verifying clients in browsers, applications, and secure systems.
Encrypted Communication – Enables secure messaging over protocols like HTTPS and TLS, including in IBM MQ.
IBM MQ has strengthened its security measures by introducing PKCS12 keystore support in version 9.4, replacing older keystore methods.
What Changed?
Before IBM MQ 9.3 LTS, Keystore passwords were stored using a separate stash file (.sth), which was required to access encrypted credentials.
From IBM MQ 9.4, the older CMS keystore format is no longer supported. This impacts AMQP and MQTT channels, which previously relied on it. Any CMS keystore detected in MQ 9.4 will cause the channel to fail and log an error.
To avoid disruptions, users must migrate to PKCS12 keystores before upgrading to MQ 9.4.
New & Improved Security Features in IBM MQ 9.3 LTS and 9.4, IBM MQ now allows direct keystore password management without needing stash files.
Use the KEYRPWD attribute in MQSC to securely store passwords for Queue Managers and for Client Applications Passwords can be managed through various options like below
KeyRepoPassword field in the MQSCO structure
MQKEYRPWD environment variable
SSLKeyRepositoryPassword attribute in the mqclient.ini file
Enhanced Password Security:
Instead of storing passwords in plaintext, IBM MQ now encrypts them automatically:
For Queue Managers: When setting a password via KEYRPWD, IBM MQ encrypts it using a secure INITKEY field. Users should update this default key for added security.
Key points:
IBM MQ 9.4 improves security with PKCS12 keystore support.
CMS keystores are no longer supported – users must migrate to PKCS12.
New encrypted password mechanisms enhance protection.
Direct keystore password management simplifies security administration.
By adopting PKCS12 keystores, organizations can ensure stronger security, better flexibility, and uninterrupted SSL/TLS functionality in IBM MQ.