OpenShift API for data protection with Multicloud Object Gateway for backing up OpenShift applications
Here in this blog, we can learn how to use OpenShift API for Data Protection with Multicloud Object Gateway for backing up OpenShift applications?
To backup your OpenShift applications, are you looking for a tool? What you need is OADP.
In the event of an unforeseen event, having a backup of your data can be essential. By using a backup, data may be swiftly recovered to assist the business in recovering while preventing downtime and data loss. Applications can be backed up and restored using functionality provided by the OpenShift API for Data Protection (OADP).
Internal pictures and Kubernetes/OpenShift objects are backed up by OADP by being saved as archive files on object storage. Persistent volumes (PVs) are backed up using snapshots by OADP. The restored objects can be filtered by namespace, PV, or label or you can restore any object in a backup. Backups can be scheduled to run at predetermined intervals.
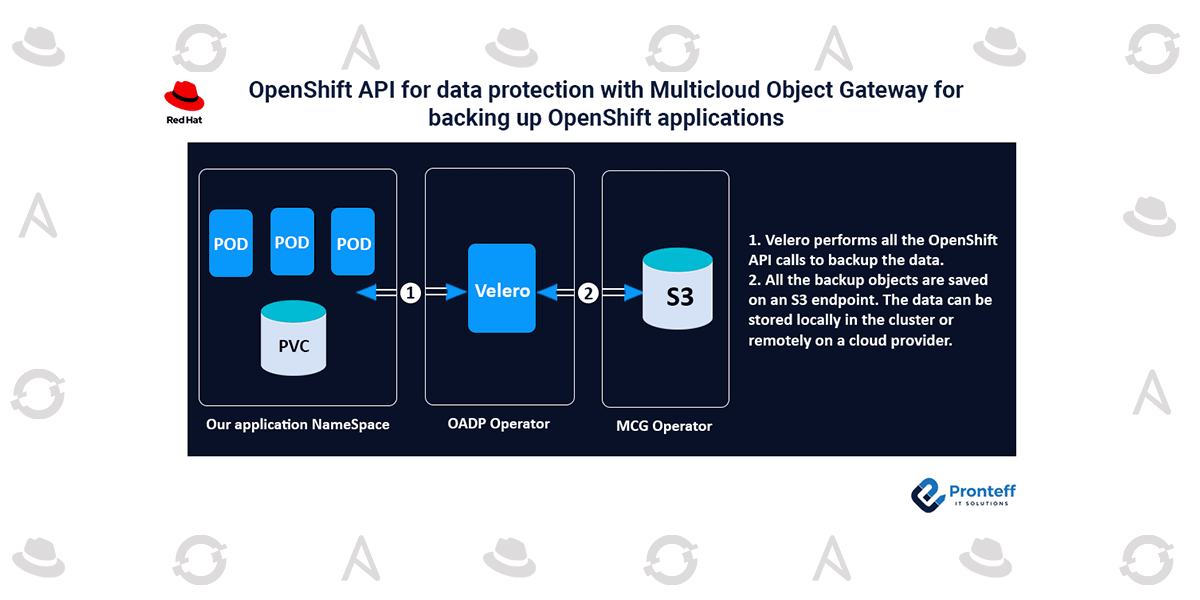
The Velero utility is made available via the default OADP plugins. Utilised to backup and restore OpenShift Container Platform resources and interface with certain cloud service providers.
The subject of this blog post is OpenShift Data Foundation’s Multicloud Object Gateway (MCG), which we will use as a backup location in this article.
We next go over the accessible parts and special resources, explain how to use OADP, and show you how to store a backup in a local S3 object storage.
The official OpenShift 4.12 documentation page has more details about OADP.
Concepts and components
OpenShift applications
Since OpenShift is a container orchestrator, when we talk about OpenShift applications, we usually refer to all OpenShift objects, normally within a Namespace. These objects include your running containerized applications (Deployments, ReplicaSets, DaemonSets, etc…), their configurations (ConfigMaps, Secrets), their networking capabilities (Services, Routes, etc), and the persistent data your application generates (PersistentVolumeClaims). An application is made up of all those objects and pieces of data, all of which must be included in a backup in order to be able to restore it in the event of a failure.
OADP
The OpenShift utility used to backup and restore Kubernetes/OpenShift cluster resources and persistent volumes is called OpenShift API for Data Protection (OADP). On the Velero project, it is based.
To backup cluster resources to a local S3 object storage, we will use OADP. Velero is set up in the Openshift cluster by the OADP Operator.
S3 Storage
S3 (Simple Storage Service) is one of the finest solutions for storing backup items because it has been the default API for remote object storage for some time. This API, which was developed by Amazon a few years ago, is currently used by a variety of companies, including the Red Hat offering with OpenShift Data Foundation. Multicloud Object Gateway (MCG), which offers an S3 storage based on NooBaa (more details below), is one of the OpenShift Data Foundation’s components. S3 is the simplest approach to save your backup objects because it is supported by nearly all of the major cloud providers.
Multicloud Object Gateway (MCG)
As was already noted, MCG is a Red Hat product that uses the S3 object storage API. MCG is a member of the OpenShift Data Foundation operator, which uses OpenShift to develop a storage solution.
The NooBaa open source project is the foundation of MCG:
NooBaa is an object data service for environments with multiple clouds and hybrid clouds. Kubernetes-based NooBaa leverages storage resources from both inside and outside the cluster with configurable placement policies to automate data use cases. It offers an S3 object store service (as well as Lambda with bucket triggers) to clients inside and outside the cluster.
This article will demonstrate how to set up an S3 bucket to store the backup locally in the cluster and how to utilise MCG to construct an S3 endpoint to store all the backup objects produced by OADP.
Prerequisites
OpenShift Data Foundation operator
To support functionalities utilised by OADP, such as CSI snapshots or the construction of an S3 bucket to house the backup objects, OpenShift Data Foundation (ODF) is necessary. The official guide describes how to install ODF using OLM. Please be aware that ODF is a meta operator that installs OCS and MCG operators, hence all references to NooBaa in this article require ODF to be installed.
Application deployment
A simple hello-openshift application will be used in this article to create a file in the cluster storage. Utilizing OADP, the application and storage will be deleted and restored from backups.
First, create the test namespace:
$ oc create namespace test-oadp
To construct a PersistentVolumeClaim, a storage request, and a deployment that builds a replica set to start one hello-openshift pod in the testing namespace while using the claim as a volume, use the configurations below:
$ cat << EOF | oc apply -f -
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: test-pvc
namespace: test-oadp
labels:
app: test-pvc
spec:
storageClassName: ocs-storagecluster-ceph-rbd
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 1Gi
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: hello-openshift
namespace: test-oadp
spec:
replicas: 1
selector:
matchLabels:
app: test
strategy:
type: Recreate
template:
metadata:
labels:
app: test
spec:
containers:
- name: hello-openshift
image: registry.access.redhat.com/ubi8/ubi
command: ["sh", "-c"]
args: ["echo \$(date) Hello OpenShift! >> /data/hello-openshift.txt && sleep 99999999"]
volumeMounts:
- name: data
mountPath: /data
volumes:
- name: data
persistentVolumeClaim:
claimName: test-pvc
EOF
Verify the status of the resources in the testing namespace:
$ oc get all -n test-oadp NAME READY STATUS RESTARTS AGE pod/hello-openshift-6bbd5697b8-svgbm 1/1 Running 0 5s NAME READY UP-TO-DATE AVAILABLE AGE deployment.apps/hello-openshift 1/1 1 1 5s NAME DESIRED CURRENT READY AGE replicaset.apps/hello-openshift-6bbd5697b8 1 1 1 5s
Verify the mounted volume where the file was created:
$ oc rsh -n test-oadp hello-openshift-6bbd5697b8-svgbm cat /data/hello-openshift.txt Tue Apr 4 11:58:43 UTC 2023 Hello OpenShift!
OADP installation and configuration
Using the Operator Lifecycle Manager (OLM), you can deploy the OADP Operator on OpenShift Container Platform 4.12. The following resources can be used to accomplish this using the OpenShift Container Platform online console or the OpenShift command-line interface (CLI):
$ cat << EOF | oc apply -f -
apiVersion: v1
kind: Namespace
metadata:
name: openshift-adp
annotations:
workload.openshift.io/allowed: management
labels:
name: openshift-adp
openshift.io/cluster-monitoring: "true"
---
apiVersion: operators.coreos.com/v1
kind: OperatorGroup
metadata:
name: redhat-oadp-operator-group
namespace: openshift-adp
spec:
targetNamespaces:
- openshift-adp
---
apiVersion: operators.coreos.com/v1alpha1
kind: Subscription
metadata:
name: redhat-oadp-operator-subscription
namespace: openshift-adp
spec:
channel: "stable"
name: redhat-oadp-operator
source: redhat-operators
sourceNamespace: openshift-marketplace
EOF
Test to see if the Cluster Service Version (CSV) is generated.
$ oc get csv -n openshift-adp NAME DISPLAY VERSION REPLACES PHASE oadp-operator.v1.1.2 OADP Operator 1.1.2 oadp-operator.v1.1.1 Succeeded
OADP custom resources
Object Bucket Claim
on the S3 endpoint where backups are kept, the bucket resource offers object storage.
Create an Object Bucket Claim by using the following resource:
$ cat << EOF | oc apply -f - apiVersion: objectbucket.io/v1alpha1 kind: ObjectBucketClaim metadata: name: obc-sample namespace: openshift-storage spec: storageClassName: openshift-storage.noobaa.io generateBucketName: test-bucket EOF
The ConfigMap and the Secret you receive after configuring the Object Bucket Claim together include all the data you need to configure the Data Protection Application resource.
Get the AWS_ACCESS_KEY_ID:
$ oc get secret obc-sample -n openshift-storage -o jsonpath='{.data.AWS_ACCESS_KEY_ID}{"\n"}' | base64 -d
AWS_SECRET_ACCESS_KEY Obtain:
$ oc get secret obc-sample -n openshift-storage -o jsonpath='{.data.AWS_SECRET_ACCESS_KEY}{"\n"}' | base64 -d
the BUCKET_HOST, please:
$ oc get cm obc-sample -n openshift-storage -o jsonpath='{.data.BUCKET_HOST}{"\n"}'
BUCKET_NAME, obtain it:
$ oc get cm obc-sample -n openshift-storage -o jsonpath='{.data.BUCKET_NAME}{"\n"}'
Data Protection Application
The desired state of OADP is specified by the custom resource for the Data Protection Application.
For OADP, you must build a Secret using the S3 endpoint credentials.
A credentials-velero file should be made:
$ cat << EOF > ./credentials-velero [default] aws_access_key_id=<AWS_ACCESS_KEY_ID> aws_secret_access_key=<AWS_SECRET_ACCESS_KEY> EOF
Make the covert item:
$ oc create secret generic cloud-credentials -n openshift-adp --from-file cloud=credentials-velero
The local MCG S3 endpoint is used in the configuration that follows. Please consult the official documentation for additional setup options.
$ cat << EOF | oc apply -f -
apiVersion: oadp.openshift.io/v1alpha1
kind: DataProtectionApplication
metadata:
name: oadp-dpa
namespace: openshift-adp
spec:
configuration:
velero:
featureFlags:
- EnableCSI
defaultPlugins:
- csi
- openshift
- aws
backupLocations:
- velero:
config:
profile: "default"
region: "localstorage"
s3Url: "http://BUCKET_HOST"
s3ForcePathStyle: "true"
provider: aws
credential:
name: cloud-credentials
key: cloud
default: true
objectStorage:
bucket: BUCKET_NAME
prefix: velero
EOF
Backup
By setting up a Backup custom resource, which generates backup files for Kubernetes/OpenShift resources and internal images on an S3 object storage as well as snapshots for persistent volumes (PVs), you may back up applications.
You may back up objects and data from your OpenShift applications using OADP, as previously mentioned. Additionally, we may use CSI (Container Storage Interface) volume snapshots with OADP to back up data kept in a Persistent Volume Claim. It is important to add the following label to your volume in order to make this function available:
$ oc label volumesnapshotclass ocs-storagecluster-rbdplugin-snapclass velero.io/csi-volumesnapshot-class=true
Obtain the name of the Backup Storage Locations that were first established as a part of the Data Protection Application. The Backup custom resource will be configured using it:
$ oc get BackupStorageLocations -n openshift-adp NAME PHASE LAST VALIDATED AGE DEFAULT oadp-dpa-1 Available 11s 31m
The resources in the testing namespace test-oadp are all backed up in the following Backup CR example. The persistent volume snapshot, internal images, and Kubernetes/OpenShift resources are all included in the backup. The official documentation contains information on many setup options.
$ cat << EOF | oc apply -f -
apiVersion: velero.io/v1
kind: Backup
metadata:
name: backup-sample
labels:
velero.io/storage-location: default
namespace: openshift-adp
spec:
hooks: {}
includedNamespaces:
- test-oadp
storageLocation: oadp-dpa-1
ttl: 720h0m0s
EOF
Check that the Backup CR’s state is Completed:
$ oc get backup -n openshift-adp backup-sample -o jsonpath='{.status.phase}'
Restore
You can restore programmes from a backup by using the Restore custom resource. Both the backup to use and the resources to restore are up to you.
We should remove our testing namespace before using the restore object:
$ oc delete namespace test-oadp
Verify that the namespace doesn’t include any resources:
$ oc get all -n test-oadp No resources found in test-oadp namespace.
You can define an array of resources to include in the restoration process in the restoration object. All resources are used if nothing else is provided. The official documentation contains more details.
$ cat << EOF | oc apply -f - apiVersion: velero.io/v1 kind: Restore metadata: name: restore-sample namespace: openshift-adp spec: backupName: backup-sample includedResources: [] excludedResources: - nodes - events - events.events.k8s.io - backups.velero.io - restores.velero.io - resticrepositories.velero.io restorePVs: true EOF
Check that the Backup CR’s state is Completed:
$ oc get restore -n openshift-adp restore-sample -o jsonpath='{.status.phase}'
Verify that the hello-openshift application resources and the testing namespace have both been restored:
$ oc get all -n test-oadp NAME READY STATUS RESTARTS AGE pod/hello-openshift-6bbd5697b8-rqw6b 1/1 Running 0 17s NAME READY UP-TO-DATE AVAILABLE AGE deployment.apps/hello-openshift 1/1 1 1 17s NAME DESIRED CURRENT READY AGE replicaset.apps/hello-openshift-6bbd5697b8 1 1 1 17s
Verify the file that was restored from the storage backup:
$ oc rsh -n test-oadp hello-openshift-6bbd5697b8-rqw6b cat /data/hello-openshift.txt Tue Apr 4 11:58:43 UTC 2023 Hello OpenShift! Tue Apr 4 12:03:29 UTC 2023 Hello OpenShift!
The backup data is printed in the first print, and the recently restored programme writes the second print.
Conclusion
Your OpenShift applications should be backed up regularly. OADP uses the OpenShift objects’ simplicity and flexibility to make it simple to configure backups and restore them if necessary. Furthermore, it’s crucial to realise that keeping your backups outside of your cluster in a hybrid cloud or multi cloud scenario is possible if you store them at an S3 endpoint.