Integrating GitHub Actions with Azure Red Hat OpenShift (ARO)
In this blog, we are going to learn about integrating GitHub Actions with Azure Red Hat OpenShift (ARO).
Organizations can create a highly automated and simplified software development and delivery process by combining Infrastructure as Code with Continuous Integration and Continuous Delivery and/or Deployment of CI/CD in cloud platforms. Using CI/CD, developers may continually integrate code changes and test the product while also defining and provisioning infrastructure resources through code. This strategy can assist businesses in delivering software more quickly and dependably while also raising the general caliber of their software.
As best practices for collaboration, automation, scalability, and security, many organizations install applications in Azure using GitHub Actions and Terraform.
What will be covered?
Learn how to deploy Azure Red Hat OpenShift (ARO) using Terraform and combine it with Terraform Cloud and GitHub Actions in this blog post.
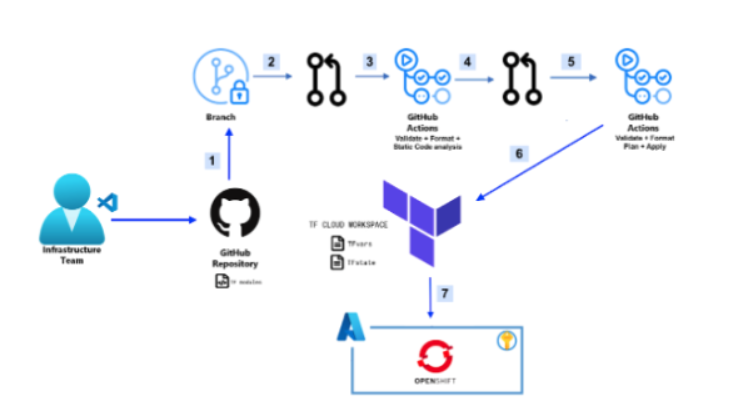
Dataflow
- Change the code and branch off from the main branch. Changing the work node instance type or subnet address are two examples.
- To the new branch, create a pull request (PR).
- To ensure that your code is correctly formatted, internally consistent, and creates a secure architecture, the GitHub Actions procedure will be initiated.
- To merge into the main branch, create a PR.
- A terraform plan will be executed via a GitHub Actions procedure. Both GitHub Actions and the Terraform cloud workspace will be able to view the plan’s outcome.
- Terraform application will run upon the team’s assessment of the PR and its merging into the main branch.
- Red Hat OpenShift will be installed on Azure through Terraform.
Workflow
It is advised that developers refrain from pushing changes immediately to the main branch in order to preserve code quality, prevent unintentional modifications, enforce policies, collaborate more effectively, and as a best practice.
Teams may make sure that essential branches are appropriately managed and maintained by adopting protected branches, which can eventually result in a more dependable and stable codebase.
The infrastructure team should push modifications to the feature/development branch after creating a new branch from the main and making changes to it. Terraform-UnitTests will be triggered by pushing to the branch.
The infrastructure team can build a pull request that will cause Terraform-Push after Terraform-UnitTests have been successfully executed.
We’ll employ two processes:
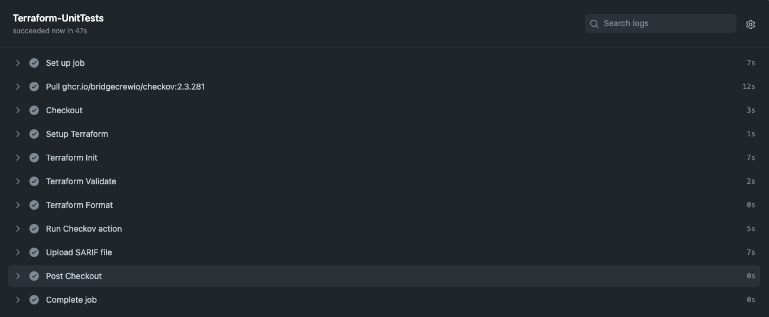
- Terraform-UnitTests.yml: Run unit tests whenever a branch is pushed using the Terraform-UnitTests.yml workflow. The format and security scans of this workflow will be examined as part of the Terraform validation process.
- Terraform-Push.yml: This workflow consists of two phases: a push phase and a merging phase.
The terraform plan command will be started and executed by this process based on each push from the feature/development branches to the main branch. When a merge request is submitted after a successful push, this procedure will launch the terraform apply command.
Prerequisites
- Active Azure Account with Subscription
- Account on Terraform Cloud
- GitHub profile
Red Hat account with Visual Studio Code, Git, Azure CLI, and Terraform CLI installed
Steps
1. Setup Azure CLI
Microsoft Azure’s command-line interface (CLI) is used to manage resources on this cloud computing platform.
Install the Azure CLI on your computer at home.
2. VM series limit increases
To make sure that your Azure Red Hat OpenShift cluster has the resources it needs to operate effectively and consistently, you must increase restrictions by VM series for installation.
150 DSv3 Family vCPUs are typical.
200 total regional vCPUs
3. Find out the Red Hat pull secret.
Sign in by going to your Red Hat OpenShift cluster manager site. Get the pull secret now. When setting up the Azure Red Hat OpenShift cluster in the Terraform Cloud, we will make use of this secret.
4. Clone the GitHub repository and fork it.
Clone the following repository to your local workstation by forking it on GitHub.
https://github.com/DexHat/aro-terra-gitactions
Update yours. git ignore file with the following information after cloning on the local workstation:
#**Secrets** pull-secret* variables_secrets*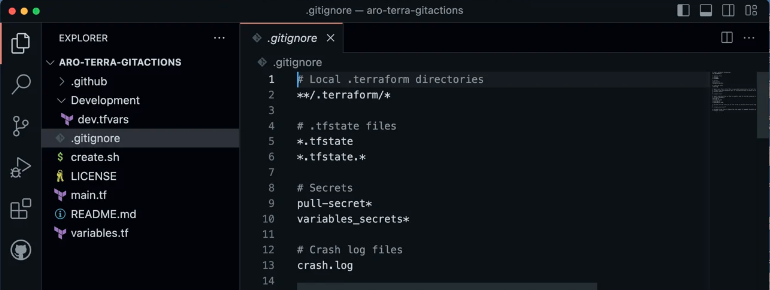
5. Use the create.sh script and set the variables
For the script creation.sh, set the following variables:
#resourcePrefix="<azure-resources-name-prefix>"
#aroDomain="${resourcePrefix,,}"
#aroClusterServicePrincipalDisplayName="${resourcePrefix}-aro-sp-${RANDOM}"
#pullSecret="${RedHat-PullSecret-Path}"
#location="${ARO-location}"
To connect to Azure, issue the az login command:
az login --use-device-code
Use the following command to run the create.sh file:
sh create.sh
t will:
- For the Azure Red Hat OpenShift cluster, create a variables-secrets file containing all the variables.
- Identify the required service providers.
- Create a service principal and give it the roles of contributor and system administrator.
- Create variables for GitHub Actions, tfvars, and Terraform Cloud.
6. Register for Terraform Cloud
We’re going to use Terraform Cloud to connect Terraform with GitHub Actions.
Create a new Terraform Cloud account first. After that, select or start a new organization.
7. Copy and set secret variables
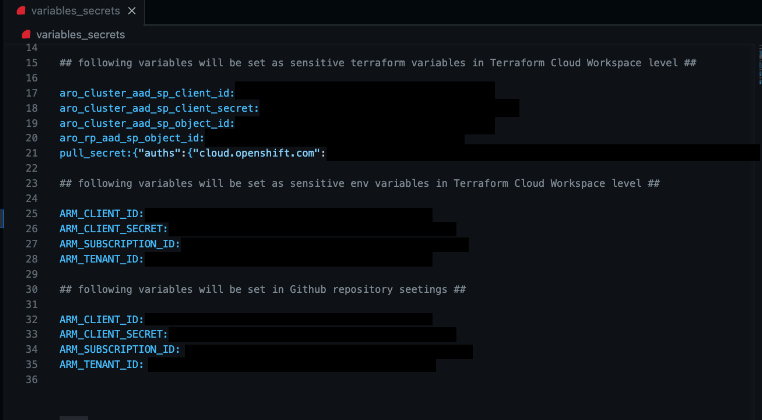
Set the following variables and secrets in the Terraform Cloud workspace level by copying them from the variables_secrets file.
terraforming parameters
Service Principal Application (client) ID: aro_cluster_aad
service principal secret value for aro_cluster_aad_sp
Service Principal Object ID: aro_cluster_aad_sp_object_id
Azure Red Hat OpenShift Resource Provider Object ID: aro_rp_aad_sp
pull_secret equals xxxx
Environmental Factors
Service Principal Application (client) ID: ARM_CLIENT_ID
Service Principal Secret Value for ARM_CLIENT_SECRET.
ID for an Azure subscription is ARM_SUBSCRIPTION_ID.
Azure Tenant ID is ARM_TENANT_ID.
Please see Protect Sensitive Input Variables for additional details regarding sensitive variables in Terraform.
We’re going to set all of the variables at the workspace level because we’re using Terraform Cloud.
8. Set up the Terraform CLI
The Terraform CLI is a potent tool for managing infrastructure as code that enables users to automate the deployment and maintenance of infrastructure resources and version control infrastructure modifications.
GitHub Actions with Terraform Cloud integration
Run Terraform login to create a token after locally installing Terraform CLI.
The GitHub Actions CI/CD pipeline will be integrated using the generated token.
Create the TF_API_TOKEN secret and paste the value from the previous step into it under the GitHub repository’s Secrets and Variables – Actions section.
Make a development environment under GitHub’s Environments section.
Different sizes and configurations of the Azure Red Hat OpenShift cluster can be deployed in various settings, such as production, staging, and development.
Set the following variables and secrets under the GitHub repository by copying them from the variables_secrets file.
- ARM_CLIENT_ID = Service Principal Application (client)
- ARM_CLIENT_SECRET = Service Principal Secret Value
- ARM_SUBSCRIPTION_ID = Azure subscription ID
- ARM_TENANT_ID = Azure tenant ID
Set the following variables and secrets in the Development/tfvars file on your local workstation by copying them from the variables_secrets file.
- domain
- location
- resource_group_name
- resource_prefix
- virtual_network_address_space
- master_subnet_address_space
- worker_subnet_address_space
9. Upload to the GitHub repository and merge.
Push Development/tfvars to your GitHub repository after upgrading it. The Terraform-UnitTests.yml file will be triggered.
You will activate Terraform-Push.yml when you merge into the main branch.
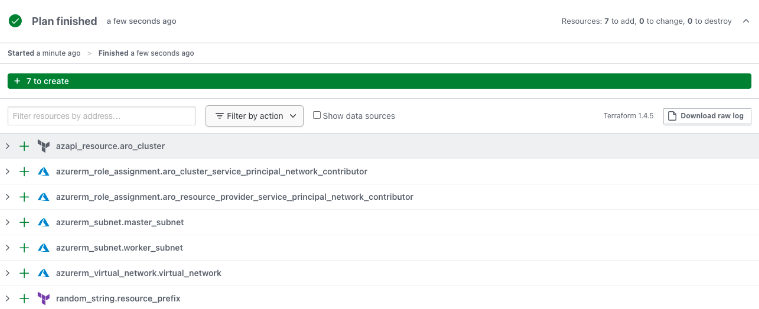
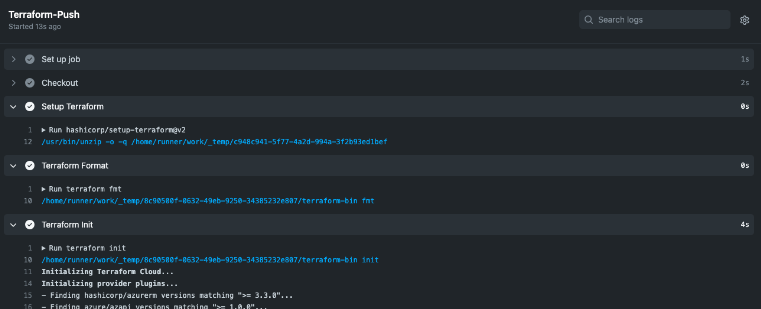
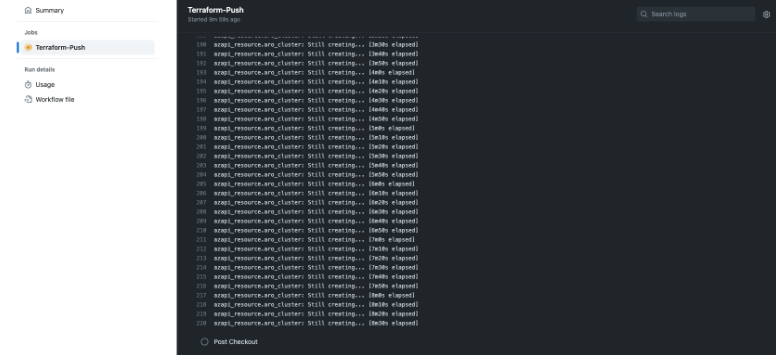
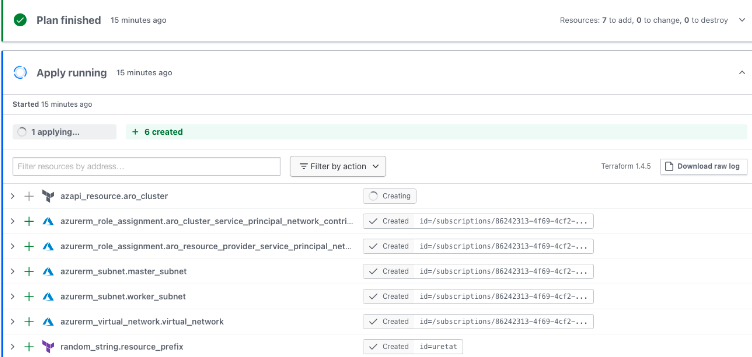
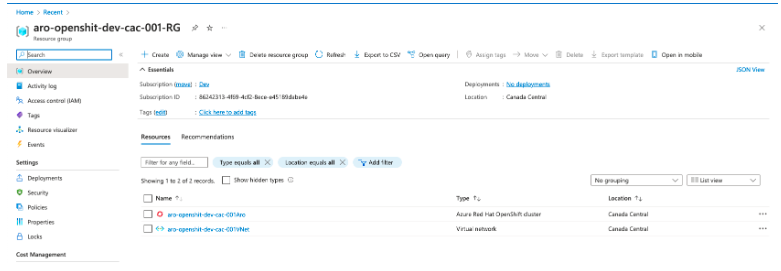
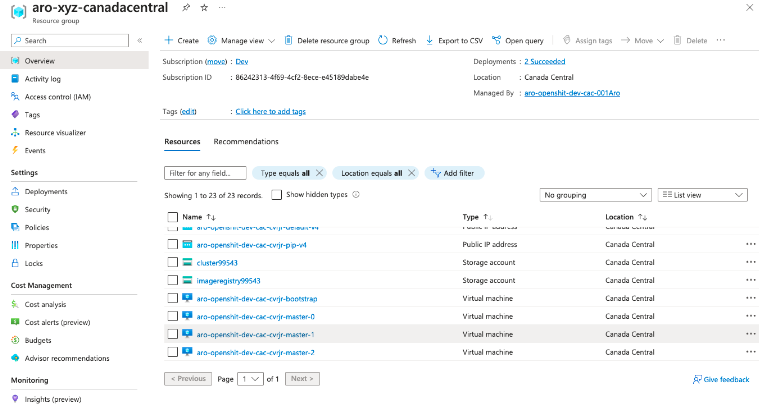
Cluster information
This method can be used to obtain cluster information:
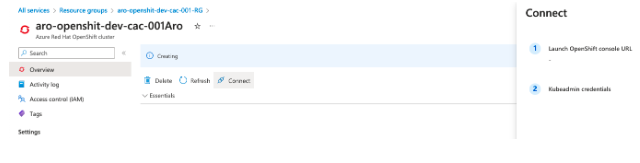
Conclusion
In conclusion, using Terraform Cloud and GitHub Actions together can offer a strong method for setting up and maintaining Azure Red Hat OpenShift (ARO) clusters. While Terraform Cloud offers a way to manage infrastructure as code in a scalable and effective way, GitHub Actions offers a way to automate and optimize the process of managing code modifications and deployments. Azure offers a stable infrastructure for hosting and administering Azure Red Hat OpenShift clusters as a cloud service provider. Organizations may deploy and operate Azure Red Hat OpenShift clusters more effectively, with better consistency and control, and with the flexibility to quickly scale up or down as necessary by utilizing these tools and services.