Automating mesh with Ansible in the cloud
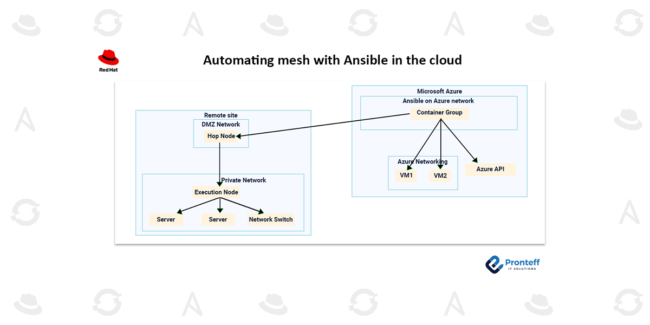
Automating mesh with Ansible in the cloud Here in this blog, we will learn about Automating mesh with Ansible in the cloud. Introduction Ansible Automation Platform’s Automation Mesh feature enables enterprises to share automation workloads amongst peer-to-peer hybrid cloud connections by leveraging their current networks. Organizations can scale their automation with a single control plane…