Red Hat OpenShift security guide for AWS
Here in this blog, we will learn about red Hat Open Shift Security Guide for AWS.
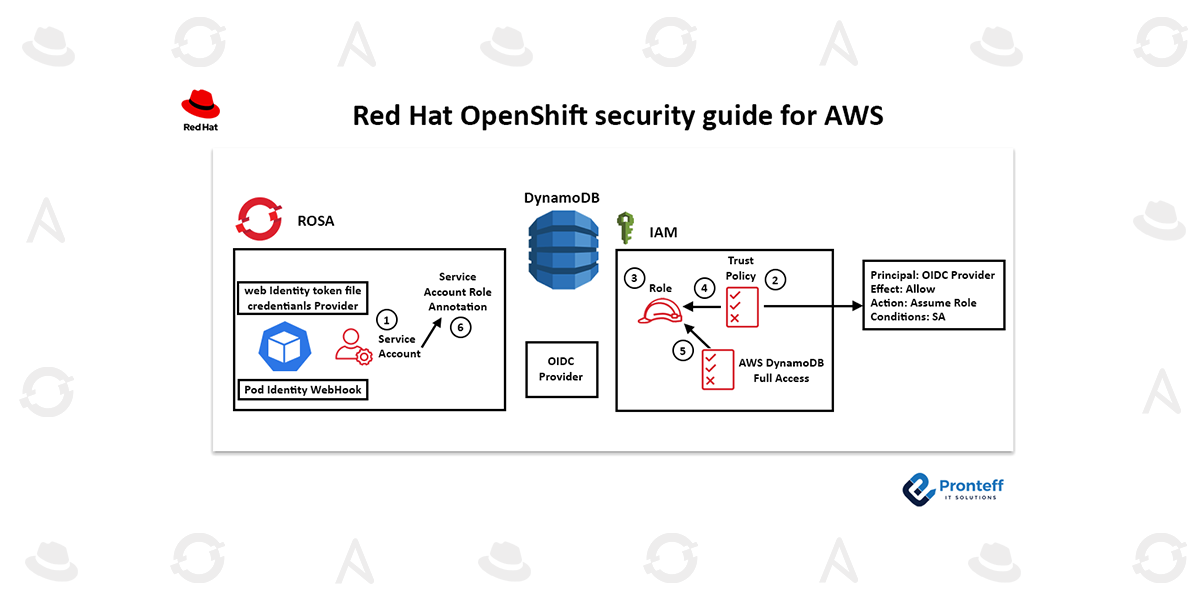
All the components required to leverage IRSA are already present in ROSA clusters. AWS Security Token Service (STS) and OpenID Connect (OIDC) are used by Red Hat OpenShift Service on AWS clusters to provide in-cluster operators with access to the required AWS resources. This enables users to access various AWS services by providing a web identity token. A client’s token is verified against the OIDC identity provider when they log in to a service via STS. Granular access control to AWS resources is made possible by utilizing STS tokens and the OIDC identity provider, which do away with the need for static AWS credentials.
The procedures to establish this safer connection are as follows:
1) In OpenShift, create a service account for your application. It is advised to run OpenShift applications with service accounts when the entity executing them requires specialized permissions. You can run your applications with an identity from service accounts, which eliminates the need to share login credentials.
2) Create a trust policy in AWS: To enable the service account from the OIDC provider (in this example, ROSA) to take on an IAM role, you must establish a trust policy in AWS. The information from the ROSA OIDC provider and permission for the sts:AssumeRole action should be included in the trust policy. As an illustration:

3/4) Establish an IAM role in AWS and associate it with the policy of trust: To specify the permissions the service account will have to access the database, create a new role in AWS IAM. Attach this role to the trust policy you made in the second step.
5) Attach the relevant database access policy to the IAM role: Ensure that the required database access policy (such as AmazonDynamoDBFullAccess for Amazon DynamoDB) is attached to the IAM role during its creation in order to specify the level of permissions that the service account will have when interacting with the database.
6) Add an annotation to the OpenShift service account indicating the IAM role it should take on when establishing a database connection.
After completing these steps, the application running within the ROSA cluster can use the Web IdentityToken File Credentials Provider and the AWS SDK to manage authentication automatically.
In order to authorize access to the database, the Pod Identity Webhook will intercept the request, verify the role and token, and acquire STS credentials. The application and the AWS database service have a smoother and more secure connection thanks to this whole behind-the-scenes procedure.
In addition to improving security, using IAM roles for service accounts and Pod Identity makes managing access permissions easier because you can update the IAM policies as needed without having to modify the application code.