Developer Preview Update for Gateway API with OpenShift Networking
Here in this blog, we are going to learn about Developer Preview Update for Gateway API with OpenShift Networking.
Red Hat has released an improved Developer Preview for Gateway API support in OCP 4.13.5 as a follow-up to the OpenShift 4.12 Developer Preview of the Gateway API. Please take a moment to go through our initial blog post, Introducing Gateway API with OpenShift Networking – Developer Preview, if you haven’t already. It provides a summary of the Gateway API’s parts.
The Developer Preview includes new functionality.
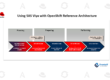
The Gateway API can now be installed and configured with the Ingress Operator thanks to this Developer Preview update, which automatically installs all required Gateway API components without requiring any further downloads. By giving the Ingress Operator control over installation and configuration, developers are free to concentrate on utilizing and exploring the robust API that the Gateway API provides.
The Ingress Operator makes the Gateway API available by:
1) Installing the custom resource definitions (CRDs) for the Gateway API version 0.5.1
2) Installing and setting up Istio for use with OpenShift Service Mesh (OSSM) as the Gateway API implementation
3) Using Istio’s automatic deployments to make it possible to create Load Balancers
4) Creating DNS Records for Gateways automatically
These enhancements make it possible for OpenShift developers to explore and use the Gateway API using Red Hat’s current range of product offerings. By fusing the Ingress Operator with OpenShift Service Mesh, we are able to provide this Developer Preview of the Gateway API with the current stable and security-focused Istio solution.
Behind a security gate
Accessible via OpenShift’s feature gate system are the features described in this Developer Preview version. Gateway API support is placed behind a feature gate so that it is not enabled by default and must be requested by the user. The “CustomNoUpgrade” feature set can be used to enable the feature gate, making the cluster ineligible for upgrades once it is activated.
On a cluster that is not in production, only enable this functionality. This feature gate cannot be turned off once it has been activated. The machine config operator will reboot each node sequentially after patching the feature gate configuration since feature gates are stored in the machine config, in accordance with your machine config pool settings.