Enhance Security Early in the Software Development Lifecycle
Here in ths blog, we are going to learn how to Enhance Security Early in the Software Development Lifecycle.
It’s no secret that open-source software has grown in popularity in recent years, giving a variety of advantages to developers. However, it is critical to note that open-source software is not immune to security threats, and vulnerabilities can occur as a result of the intricate interdependencies within the software ecosystem.
One of the most recent examples demonstrating the significance of addressing security threats is the log4j vulnerability, sometimes known as “log4shell.” Log4j is a popular Java-based logging library used in a variety of applications, however in December 2021, a significant vulnerability was identified that allowed attackers to remotely execute arbitrary code. This vulnerability has a substantial impact on many businesses, emphasizing the significance of proactively managing and safeguarding open-source dependencies.
The Heartbleed vulnerability, which exposed a significant security hole in the OpenSSL cryptographic library, is another prominent example. Many websites and applications were impacted by this vulnerability, which allowed attackers to obtain sensitive data such as passwords and private keys. The incident served as a wake-up call to enterprises to emphasize open-source dependency security and actively monitor for vulnerabilities.
To address these issues, the Software Bill of Materials (SBOM) has developed as an important instrument for improved supply chain security. With SBOM, businesses can simply track all software components and their dependencies within a containerized application, including open-source libraries and frameworks.
This level of insight allows for quick upgrades and patches, lowering the chance of known vulnerabilities being exploited and creating a more secure application environment. If you’re utilizing Red Hat OpenShift, you can use SBOM to improve supply chain security even further. OpenShift offers a robust container orchestration and management platform, making it a suitable setting for implementing SBOM techniques.
Integrating a shift left strategy into the software development lifecycle prioritizes security measures early in the software development lifecycle, ensuring proactive vulnerability monitoring and increased supply chain security for containerized applications. By adding SBOM into your vulnerability management processes, you can more effectively discover, prioritize, and resolve security threats, cooperate with upstream open source communities for patches and updates, and create a strong supply chain security framework. With this technique, you can maintain a more secure containerized environment in OpenShift while benefiting from the flexibility and creativity of open-source projects.
Sigstore Code Signing: Maintain Software Authenticity and Integrity
In today’s interconnected world, code signing is critical for ensuring a secure software supply chain. Sigstore is a Red Hat OpenShift open source project that provides a safe and decentralized way to code signing.
It simplifies the code signing process while also improving overall security by providing a verifiable trust trail. It is simple to integrate Sigstore into the development and deployment workflow, guaranteeing that container images and software artifacts are signed as part of the CI/CD pipeline.
Organizations can reliably launch containerized apps knowing their software has not been altered with by embracing code signing with Sigstore.
Use OpenShift Pipelines, Tekton Chains (Tech Preview), and Cosign to implement image security policies and image signing.
Organizations can improve the security of their containerized applications in Red Hat OpenShift by defining image security policies and employing image signing technologies such as Tekton Chain and Cosign. Before deployment, these checks guarantee the authenticity and integrity of container images.
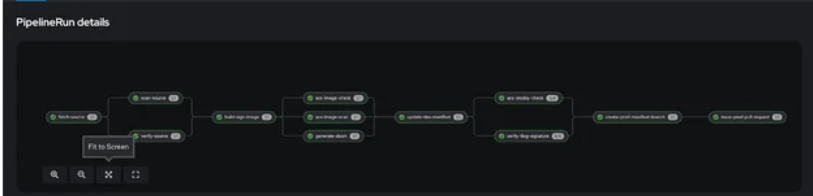
Image security policies enable enterprises to create criteria for image sources, access controls, and vulnerability scanning. By following these criteria, only trusted and certified photos can be deployed, lowering the danger of compromised or susceptible images.
Tekton Chain, when used with OpenShift Pipelines, enables enterprises to create a secure supply chain for container images. It enables developers to sign pictures with Cosign, ensuring authenticity and integrity. This cryptographic signing technique ensures that the images have not been tampered with.
Red Hat Advanced Cluster Security (RHACS)
Policy can be used to improve security even further. This policy validates container image signatures before deployment, ensuring that only images with valid and trustworthy signatures are authorized.

Organizations can develop a strong and secure image distribution process in Red Hat OpenShift by defining image security policies, employing Tekton Chain with Cosign, and incorporating RHACS. These safeguards guard against manipulated or unauthorized images, ensuring the integrity and validity of containerized applications.
Continuous Security Scanning and Remediation
RHACS is an amazing solution that can considerably help enterprises using Red Hat OpenShift containerized systems. Its continuous monitoring and automated remediation capabilities make it an essential component of the CI/CD process. RHACS integrates smoothly into the workflow, putting security first throughout the software development lifecycle.
Organizations can execute security scans and inspections at every stage of the deployment process when RHACS is incorporated into the CI/CD pipeline. This means that vulnerabilities, misconfigurations, and policy violations can be recognized early and fixed before they reach production environments.
By utilizing its APIs and CLI tools, RHACS may be readily incorporated into CI/CD workflows. As part of the build process, security scans and assessments can be initiated, ensuring that only secure and compliant artifacts get through the pipeline. Any detected security concerns are automatically highlighted, and the CI/CD pipeline is interrupted or adjusted to resolve these issues as soon as possible.
RHACS also delivers security insights and reports to assist development teams in assessing their applications’ overall security posture. These insights can be utilized to improve security procedures across the CI/CD process, ensuring that security considerations are incorporated from the beginning.
Organizations may enforce security policies, execute security scans, and automate remediation processes by embedding RHACS into the CI/CD process. This fosters a strong security culture and establishes security as an essential component of the software development lifecycle in Red Hat OpenShift.
Wrap up
Finally, integrating code and image security policies, image signing, and continuous security scanning with Red Hat OpenShift is critical for confirming the authenticity and integrity of container images. By incorporating these techniques into your CI/CD process, you may discover and resolve vulnerabilities early in development, encouraging trust throughout the software supply chain. You can reliably execute containerization with Red Hat OpenShift while prioritizing the security and integrity of your software supply chain, protecting your apps, and preserving your data.
The Secure Supply Chain blog series is intended to give you with the knowledge and practical insights you need to secure your containerized apps using Red Hat solutions. Stay watch for future posts in which we will delve deeper into each component, offering thorough information and specific strategies to improve supply chain security.