IBM Sterling Perimeter Server
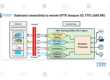
Here in this blog, we are going to learn about IBM Sterling Perimeter Server. IBM Sterling Perimeter Server a software program for managing communications that can be put in a DMZ zone. The perimeter server controls the information flow between the TCP-based transport adapters and your network’s outer layers. In high-volume, Internet gateway environments, a perimeter server can address issues with network congestion, security, and scalability.
In order to offer an extra layer of protection, a perimeter network is a computer network that is positioned between a secure internal network and an insecure exterior network. Through perimeter services, a perimeter server can communicate with Sterling B2B Integrator. The subsystem allowing multi-homing and secure perimeter network traversal for B2B communications protocols is known as perimeter services. A comparable perimeter client is necessary for a perimeter server.
The following elements make up perimeter services:
- Installing a perimeter server on a computer in your DMZ or in a more secure network is known as remote perimeter server.
- Sterling B2B Integrator’s local perimeter server already has it installed.
- Communications adapters in Sterling B2B Integrator use the perimeter services API to access the local and remote perimeter servers for multi-homing and perimeter network traversal capabilities.
- Components of the Sterling B2B Integrator’s configuration management system for perimeter servers.
By relocating security risks away from your secure network and data, perimeter servers improve security by reducing network congestion issues and scalability for large volume environments.
The configuration of a perimeter server and each adapter that interacts with the neighbourhood perimeter server must be done on the same node. A node is a single installation of the Sterling B2B Integrator. Multiple configured perimeter servers (local perimeter servers) may be connected to a single node.
A perimeter server for one trade partner with huge files and low transaction traffic can be set up, while a second perimeter server for a different trading partner with smaller files and high transaction volume can be set up on the same node.
Features of IBM Sterling Perimeter Server:
Secure Data Exchange: The Sterling Perimeter Server facilitates secure data exchange between trading partners through encrypted communication channels, ensuring the confidentiality and integrity of sensitive business data.
Trading Partner Management: It allows you to manage and on board trading partners easily, enabling seamless collaboration with various partners in your B2B ecosystem.
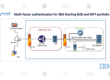
Protocol Support: The Perimeter Server supports multiple communication protocols like AS2 (Applicability Statement 2), SFTP (SSH File Transfer Protocol), FTPS (FTP Secure), Connect Direct and HTTPS, enabling flexible and secure data exchange options.
Firewall and Security: The server acts as a firewall, protecting your internal systems from direct exposure to the internet, thereby minimizing potential security risks.
Load Balancing and High Availability: It supports load balancing and high availability configurations to ensure reliable and scalable data exchange capabilities.
Integration with IBM Sterling B2B Integrator: As part of the larger IBM Sterling B2B Integrator suite, the Perimeter Server seamlessly integrates with other components for end-to-end B2B data integration and management.