OpenID Connect Security in API Connect
Here in this blog, we are going to learn how OpenID Connect Security in API Connect.
OpenID Connect:
OpenID Connect is an authentication (verifies the identity of a user or service) protocol that works with OAuth to control user access to resources. You can use OIDC in conjunction with OAuth to determine a user’s authorizations and JSON Web Tokens (JWT) to authenticate the user.
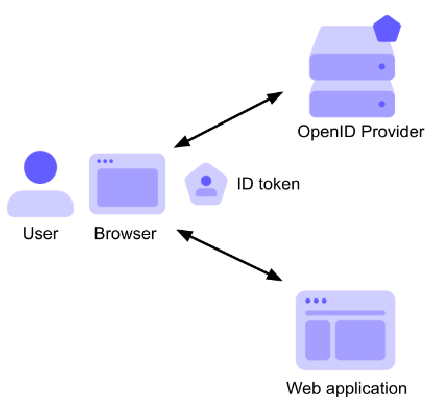
Flow for ID token:
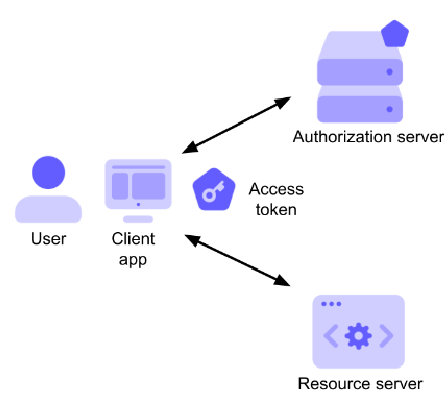
Flow for Access token:
Let’s configure in API Connect.
1. Go to API Manager in that go to resources>>user registries.create a user registry. Give the Authorization url.
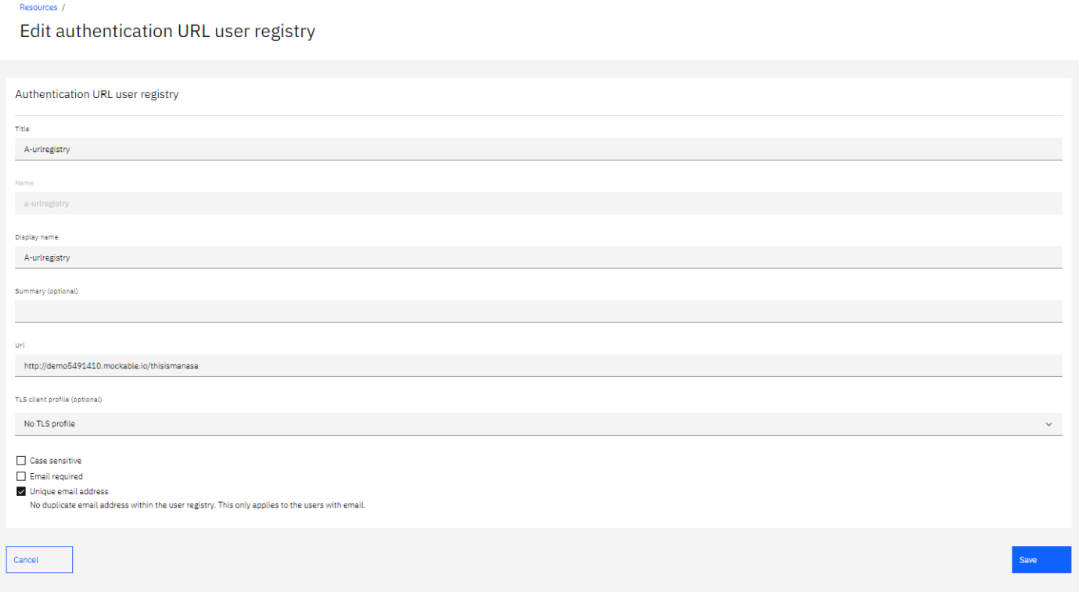
Click on save.
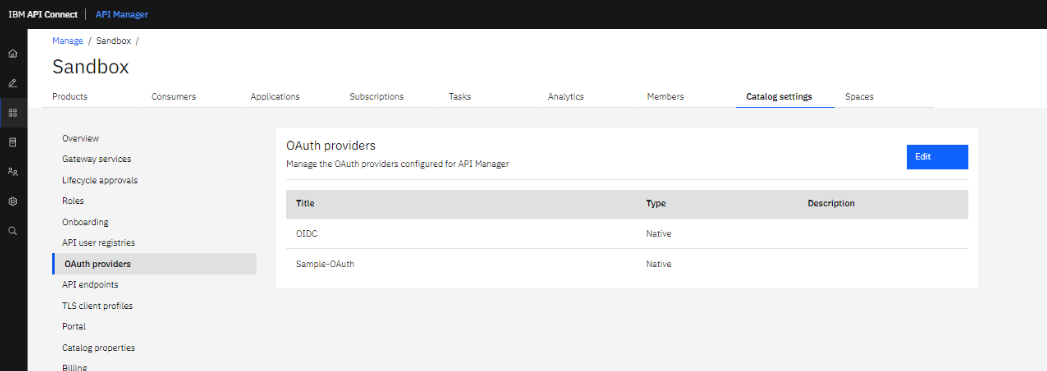
2. Next go to OAuth providers. And create an OAuth flow with OpenID connect.
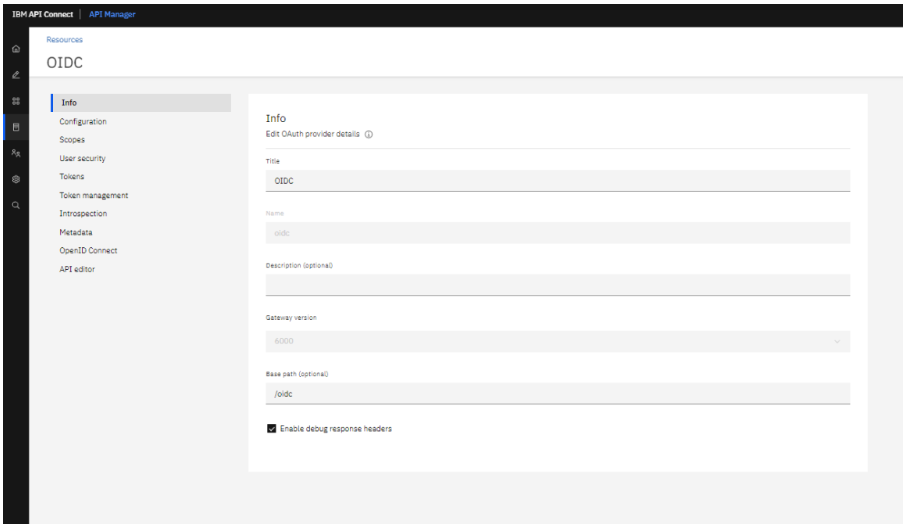
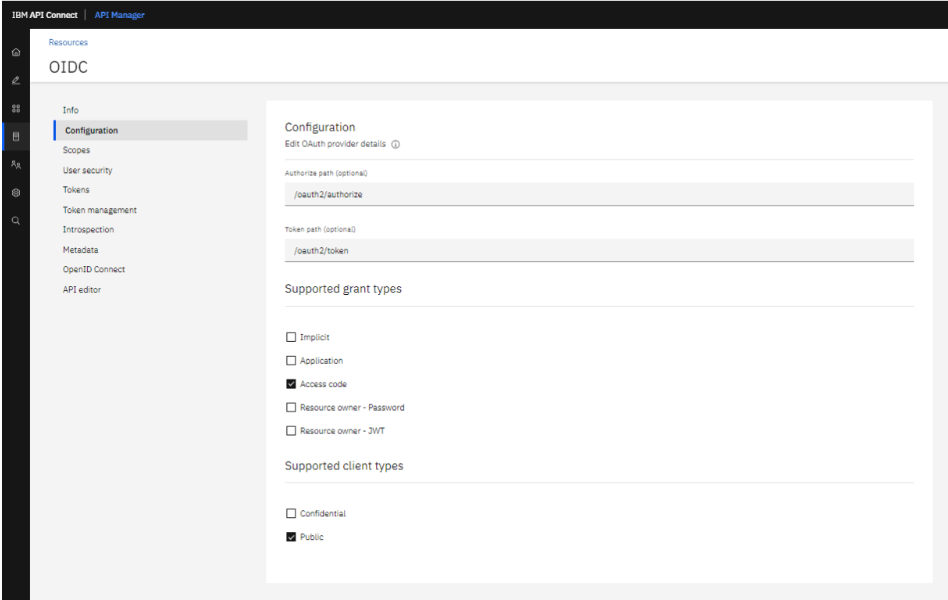
Note: OpenID Connect settings are applicable only if your selected grant types include one or more of the following: Implicit and Access code.
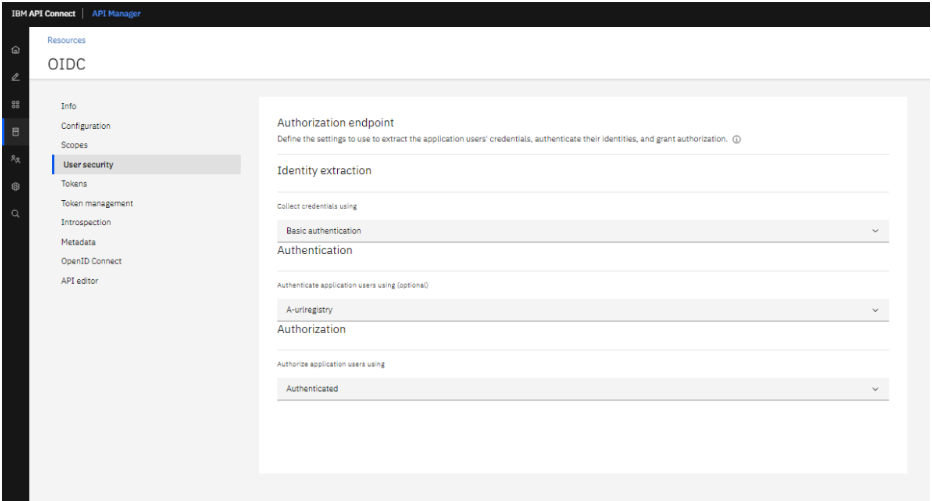
Use the user registry which has been configured earlier in user security.
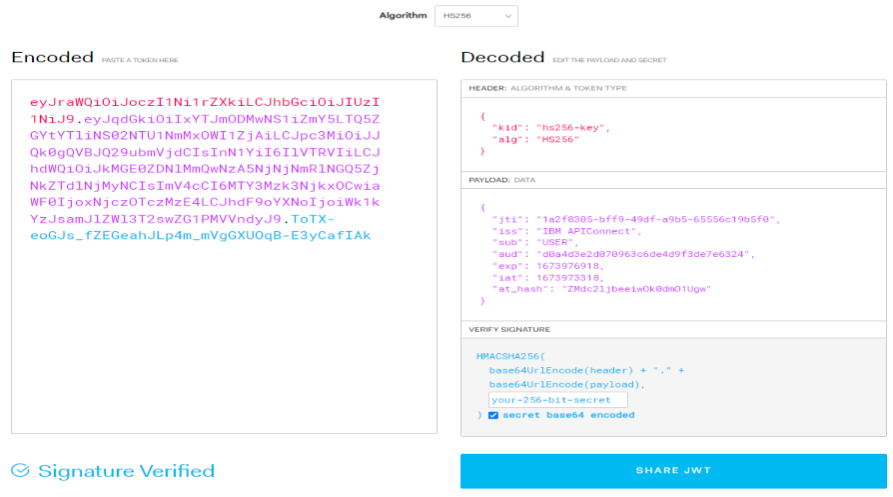
Use the id token signing key as:{ “alg”: “HS256”, “kty”: “oct”, “use”: “sig”, “k”: “o5yErLaE-dbgVpSw65Rq57OA9dHyaF66Q_Et5azPa XUjbyP0w9iRWhR4kru09aFfQLXeIODIN4uhjElYK Xt 8n76jt0Pjkd2pqk4t9abRF6tnL19GV4pflfL6uvVKkP4weOh39tqHt4TmkBgF2P-gFhgssZpjwq6l82fz3dUhQ2nkzoLA_CnyDGLZLd7SZ1yv73uzfE2Ot813zmig8KTMEMWVcWSDvy61F06vs_
6LURcq_IEEevUiubBxG5S2akNnWigfpbhWYjMI5M22FOCpdcDBt4L7K1-yHt95Siz0QUb0MNlT_X8F76wH7_A37GpKKJGqeaiNWmHkgWdE8QWDQ”, “kid”: “hs256-key”}
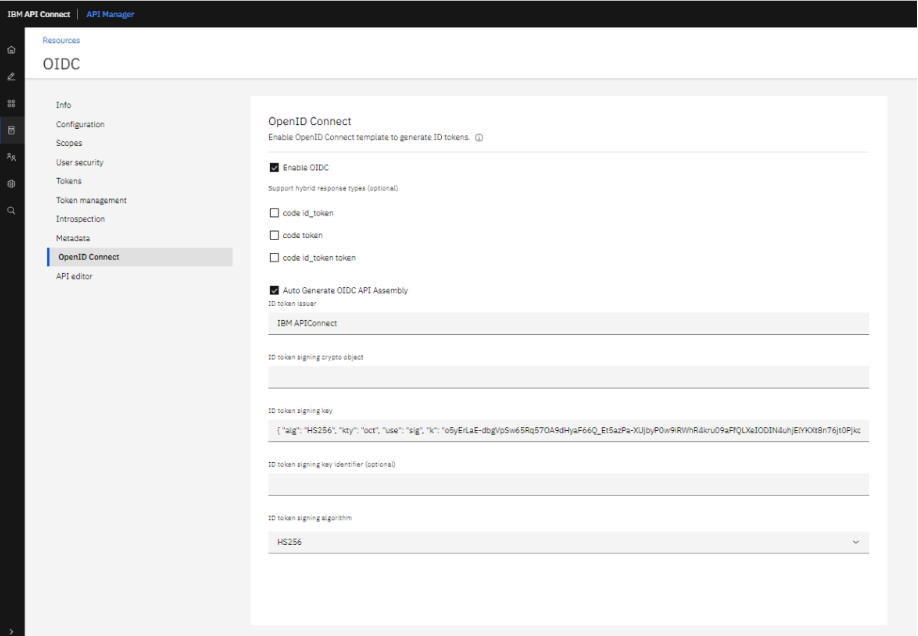
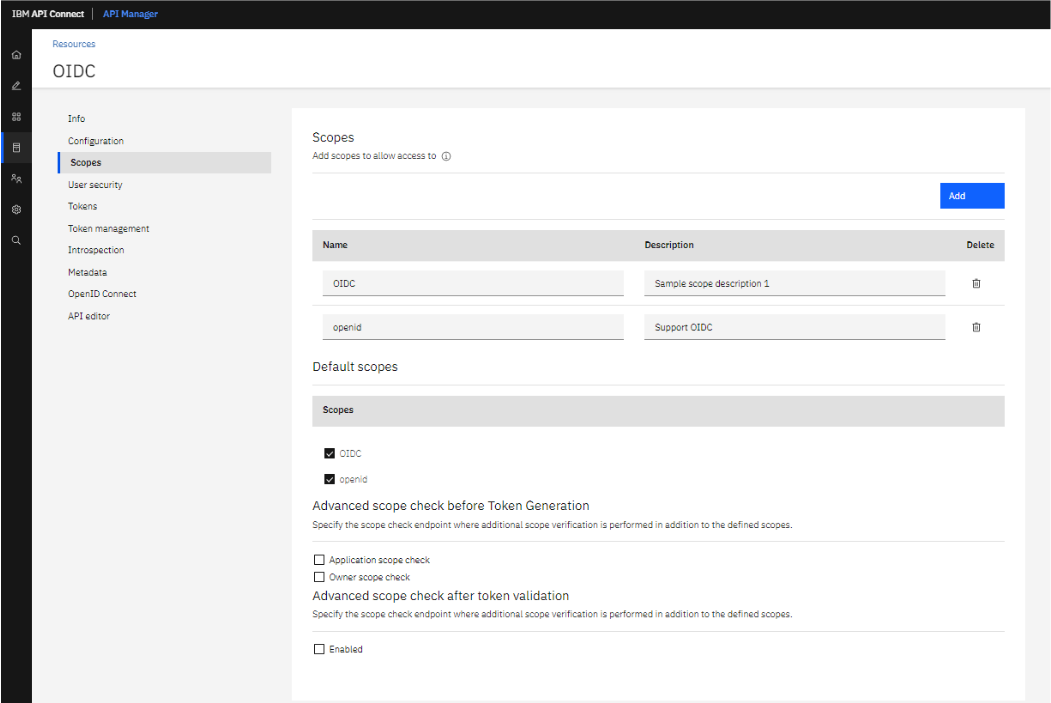
When we enable the OpenID Connect then automatically a scope will generate.
Next add the OAuth provider API and API user registry (A-urlregistry) to catalog
And apply the OAuth provider API to Consumer API.
Add security schemas.
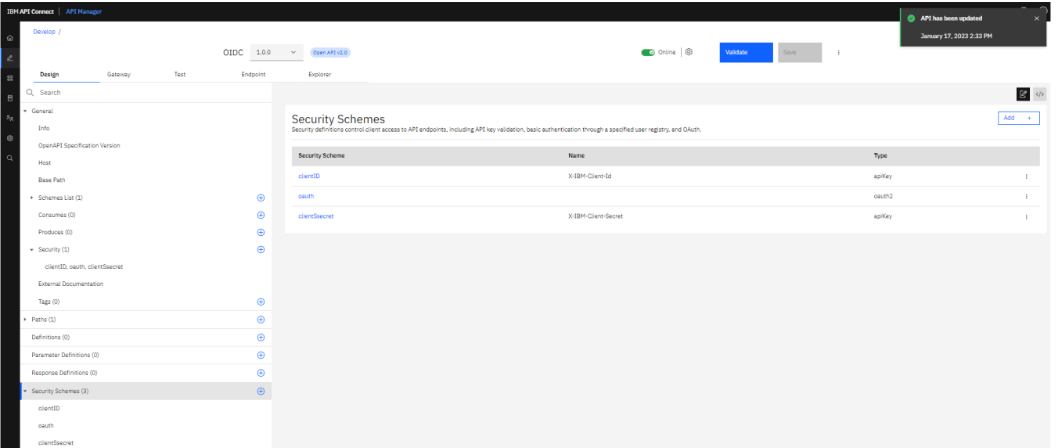
Add the OAuth which we created earlier.
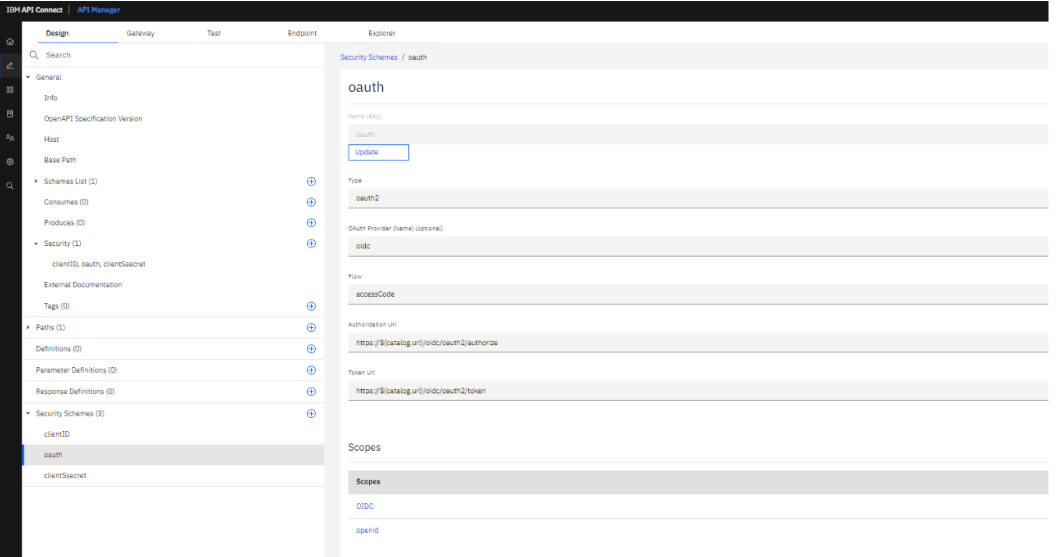
Add the security schemas in security.
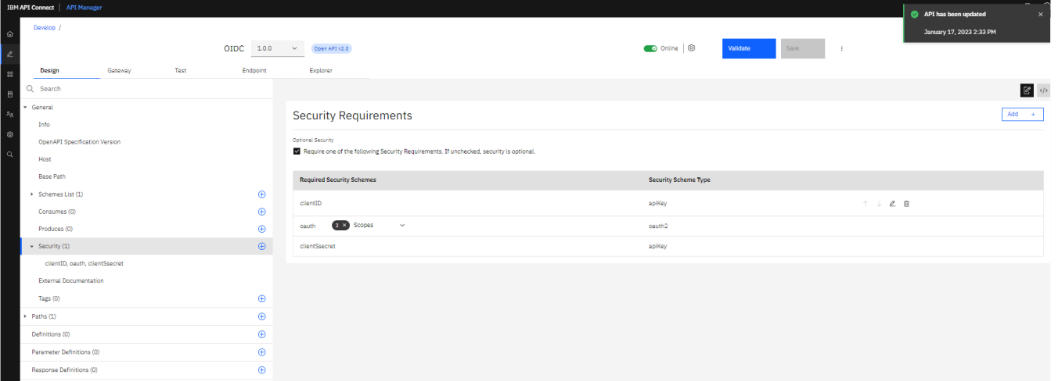
Configuring the backend URL in invoke backend URL: http://demo5491410.mockable.io/thisisanusha%3Fid=789&name=anusha
Note: We need to add the redirect URL in application.
We get three URL’s:
API Endpoint: https://uatdevelopment.prontefflabs.com:9443/nagababu/sandbox/a-accesscode/
Authorization URL:
https://uatdevelopment.prontefflabs.com:9443/nagababu/sandbox/oidc/oauth2/authorize
Token URL: https://uatdevelopment.prontefflabs.com:9443/nagababu/sandbox/oidc/oauth2/token
For code:
>>browse the below url:
https://uatdevelopment.prontefflabs.com:9443/nagababu/sandbox/oidc/oauth2/authorize?http://demo5491410.mockable.io/thisismanasa&response_type=code&scope=openid+OIDC&client _ id=d0a4d3e2d070963c6de4d9f3de7e6324
>After browsing we get below url:( get the code value)
http://demo5491410.mockable.io/thisismanasa?code=AAIEQXca5enjAkyo2ayDSOM0UVVAMekSEu78m7BxtbSqiRmRb20gjsx81ckkHTTkQnhgYDcoO5p
iWfEa9VxYVDE7lWC033K5pjebqwpcHfxPvA
To get the access token go to postman and hit the token url as below.
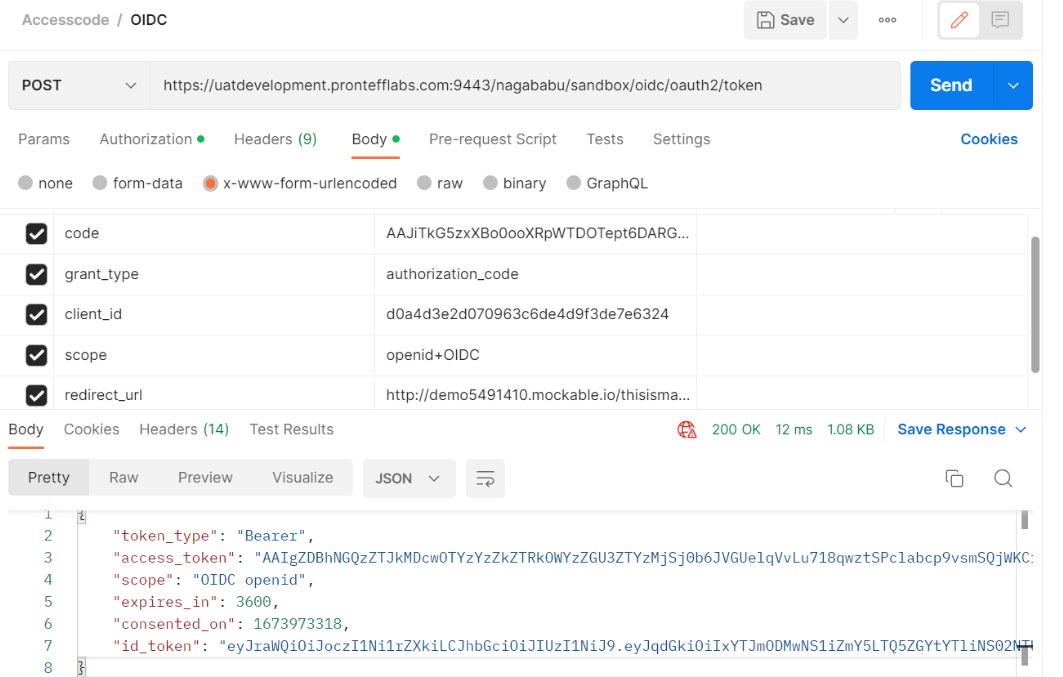
Now go to jwt.io site to verify the id_token.