Overview of Red Hat OpenStack Platform’s security
Here in this blog, we are going to learn the overview of Red hat Openstack Platform’s security.A variety of security capabilities are offered by the highly secure Red Hat OpenStack Platform to guarantee the security of your infrastructure and data.
Features consist of:
- Identity and Access Management (IAM):Red Hat OpenStack Platform interacts with the Keystone identity service, which offers centralized authentication and authorisation techniques, for identity and access management (IAM). Username/password, token-based authentication, and connection with third-party authentication providers like LDAP and Active Directory are all supported by Keystone.
- Role-Based Access Control (RBAC): Based on user roles, RBAC enables administrators to design granular access control policies. This guarantees that each user within the OpenStack system has the proper permissions and access rights.
- Network Segmentation: The networking component Neutron is used by Red Hat OpenStack Platform to offer network segmentation. In order to keep tenant networks separate from one another, it supports VLAN, VXLAN, and Software-Defined Networking (SDN) technologies and enables the establishment of virtual networks.
- Secure Hypervisor: KVM serves as the hypervisor on compute nodes in Red Hat OpenStack Platform, which supports the libvirt driver. Strong security mechanisms were implemented into this hypervisor to guard against unauthorized access, attacks involving virtual machine egress, and safe tenant isolation.
- Secure Images: Glance, the image service included in Red Hat OpenStack Platform, offers a secure image repository for virtual machine templates. To guarantee that only reliable and unaltered photos are used to build instances, photographs can be digitally signed and authenticated.
- Encrypted Storage: Cinder, a part of Red Hat OpenStack Platform’s block storage system, enables encryption for Cinder volumes. This makes sure that information kept on volumes is secure and that only authorized users may access it.
- Secure Object Storage: Data encryption at rest is supported via the Swift object storage service, which is integrated with Red Hat OpenStack Platform. Server-side encryption can be used to encrypt data saved in Swift, protecting the confidentiality and integrity of the stored objects.
- Observability: The Service Telemetry Framework (STF), a feature of Red Hat OpenStack Platform, offers an automated collection of data from remote clients, such as Red Hat OpenStack Platform or third-party nodes, and transmits that data to a centralized source for Red Hat OpenShift Container Platform deployment to receive for storage, retrieval, and monitoring. Metric, which is a numerical measurement of an application or system, and Event, which are irregular and discrete occurrences that happen in a system, are two different types of data that STF can gather. The client-required collection components are small and lightweight. All clients and the deployment share a multicast message bus, which offers quick and dependable data delivery. The deployment of additional modular data receiving and storage components in containers on Red Hat OpenShift.
- By default, SELinux (Security-Enhanced Linux) integration is included with Red Hat OpenStack Platform. By implementing necessary access controls and limiting unauthorized access to system resources, SELinux adds an extra layer of protection.
To monitor the cloud environment for potential security threats, Red Hat OpenStack Platform can be coupled with third-party Intrusion Detection and Prevention System (IDPS) products. Network attacks, unauthorized access attempts, and other security breaches can all be found and stopped by IDPS systems.
It’s crucial to remember that the security features in Red Hat OpenStack Platform can be improved and tailored in accordance with particular deployment needs and organizational security guidelines. The ongoing security updates and continual security assessments are also essential for preserving the overall security of an OpenStack system.
Red Hat OpenStack Platform: Why Use It?
Benefits of Red Hat
In this situation, choosing the appropriate on-premise private cloud platform is crucial. With built-in service hardening and key management, Red Hat OpenStack Platform offers the essential components you need for infrastructure security. It also offers data integrity with on-the-fly and at-rest encryption.
Red Hat offers 10 years of RHEL lifetime support and up to 5 years of Red Hat OpenStack Platform lifecycle support. Red Hat supports the whole stack, including host Linux, KVM, OpenStack, supported CEPH storage (in collaboration with IBM), and CEPH storage.
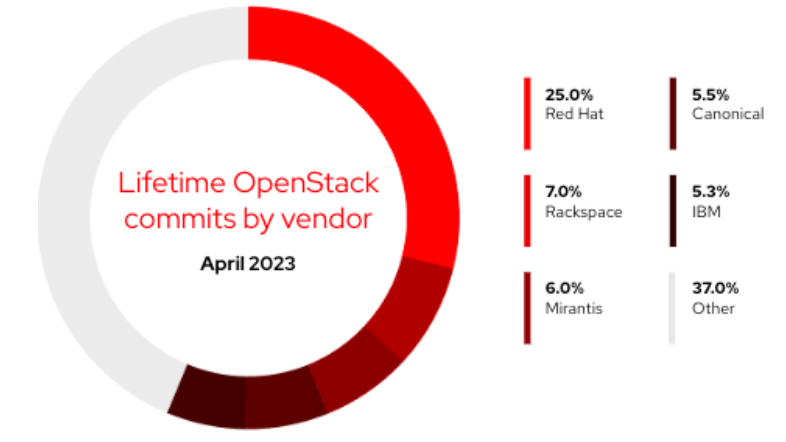
Red Hat is a leader in contributions to the upstream OpenStack community, allowing Red Hat to support the client through deployment. This is made possible by Red Hat’s upstream first attitude, which forbids us from building forks or one-off snowflakes at customer sites.
We can serve the customer end-to-end: host Linux, KVM, OpenStack, guest OS thanks to Red Hat’s certification of RHEL, Windows, and SUSE Linux guest operating systems.
Finally, Red Hat offers a Security and Hardening Guide that offers conceptual knowledge about hardening the security of a Red Hat OpenStack Platform system as well as good practice recommendations.
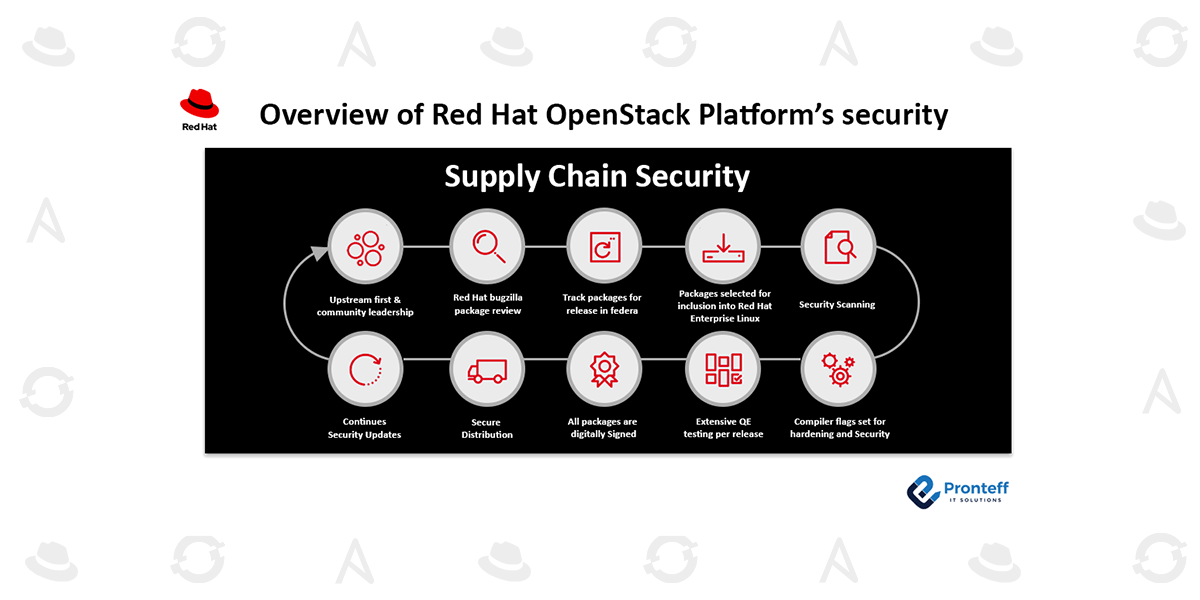
Supply Chain Security
Red Hat has a committed team that monitors, spots, and swiftly responds to vulnerabilities in its products. For all Red Hat versions in their supported life cycles (including backported fixes), you get security patches from Red Hat (that Red Hat has written, tested, and delivered). In addition, Red Hat makes the technical investments necessary for products to be certified as meeting strict governmental and commercial security standards (such FIPS 140-3).
Red Hat must continue to engage with the community and upstream partners as part of the Secure Software Supply Chain (SSSC) to support the initial focus on security. To do this, Red Hat must:
depending on the performance and security records of the packages when choosing and configuring them.
Instead of only accepting upstream builds’ compiler choices at build time, building binaries from the related source code.
use a variety of inspection and quality control methods to thwart any security flaws and regressions.
distribute all published packages via channels with cryptographically validated distribution signatures.
supplying a solitary, unified method of patching and updating.
Here, you may find out more details about SSSC.
.