Unleashing the Power of Identity and Access Management
Here in this blog, we are going to learn about Unleashing the Power of Identity and Access Management.
Introduction
In the realm of cloud computing, effective identity and access management (IAM) is vital to ensure secure and controlled access to resources. Amazon Web Services (AWS) Identity and Access Management (IAM) provides a robust set of features and capabilities to manage user identities, define fine-grained permissions, and safeguard AWS resources. In this blog post, we will explore the key features of AWS IAM and present an essay-style approach to understanding its intricacies.
1. IAM Features Overview
AWS IAM offers a comprehensive suite of features to meet the complex access control requirements of modern cloud environments. Here are some prominent features:
a. User Management: IAM allows you to create and manage user accounts, granting unique access credentials to individuals who need to interact with AWS resources. This includes assigning user roles, enabling multi-factor authentication (MFA), and managing user passwords.
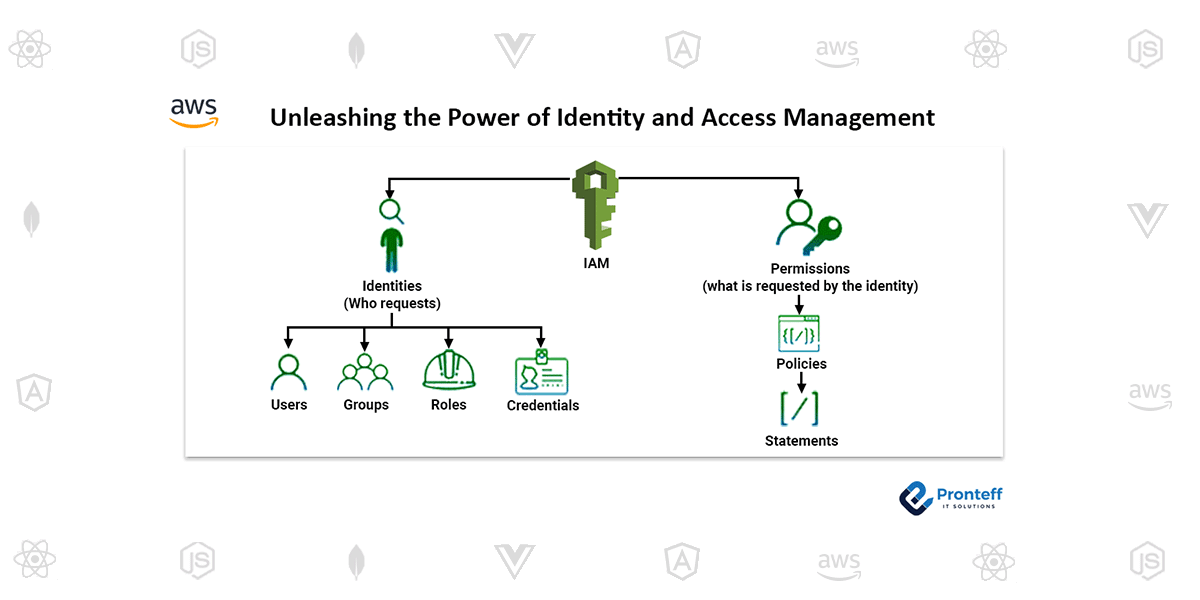
b. Groups and Roles: IAM groups enable you to logically organize users and assign permissions collectively. Roles, on the other hand, allow you to define a set of permissions that can be assumed by trusted entities such as AWS services or applications.
c. Fine-Grained Permissions: IAM provides granular control over access permissions through policies.The acts that are permitted or prohibited on AWS resources are laid out in policies, which are JSON documents. This enables you to follow the principle of least privilege and ensure that users and roles have only the necessary permissions.
d. Multi-Factor Authentication (MFA): IAM supports MFA, adding an additional layer of security by requiring users to provide an extra authentication factor, such as a hardware token or a virtual MFA app, along with their password.
e. Identity Federation: IAM integrates with external identity providers (IdPs) such as Active Directory Federation Services (ADFS), allowing you to federate identities from your existing user directories and enable single sign-on (SSO) experiences.
f. Cross-Account Access: Using IAM, you can give users or roles access to resources in one AWS account while preventing them from doing the same in another AWS account. This facilitates secure collaboration and resource sharing between different accounts.
g. IAM Access Analyzer: IAM Access Analyzer helps you identify unintended access to your AWS resources by continuously analyzing resource policies and generating actionable insights to ensure least privilege access.
2. Essay-style Approach to Understanding IAM
To gain a comprehensive understanding of AWS IAM, follow this essay-style approach:
a. Introduction: Begin by explaining the significance of IAM in cloud environments and how it forms the cornerstone of secure access control in AWS.
b. IAM Components: Describe the key components of IAM, such as users, groups, roles, and policies. Explain their roles and relationships, and how they collectively enable effective access management.
c. Policies and Permissions: Delve deeper into IAM policies and their structure. Explain how policies define permissions using JSON syntax, including actions, resources, and conditions. Emphasize the importance of using least privilege principles to minimize the attack surface.
d. User Management: Discuss the process of creating and managing IAM users, including assigning access credentials, enforcing MFA, and managing passwords. Highlight the benefits of centralizing user management in IAM.
e. Federating Identities: Explain the concept of identity federation and its advantages. Illustrate how IAM integrates with external identity providers (IdPs) to enable seamless SSO experiences and streamline user access to AWS resources.
f. Fine-Grained Permissions: Explore the concept of fine-grained permissions and the role of IAM policies in defining them. Discuss the use of conditions in policies to further refine access control based on various factors such as time of day, source IP address, or resource tags.
g. Security Best Practices: Provide a list of best practices for secure IAM implementation, including regular review of permissions, enforcing MFA,
using IAM roles for applications and services, and leveraging IAM Access Analyzer to identify potential security risks.
h. Auditing and Monitoring: Highlight the importance of auditing and monitoring IAM activities using AWS CloudTrail and AWS Config. Discuss how these services can help track changes, detect suspicious activities, and maintain compliance.
i. Conclusion: Summarize the key features and concepts discussed, emphasizing the role of IAM in securing AWS resources. Stress the significance of adopting IAM best practices and continuous monitoring to maintain a robust and secure IAM implementation.
Conclusion
AWS IAM is a powerful and versatile identity and access management service, offering a range of features to control access to your AWS resources effectively. By understanding its key components, policies, and best practices, you can establish a secure and efficient IAM framework, ensuring that the right users have the right level of access to your AWS environment.