The Key Security Features of OpenStack
Here in this blog, we are going to learn the Security Features of Open Stack.
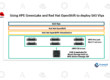
Two essential components, Barbican and Keystone, are at the core of Openstack security and are in charge of secret management and identity management, respectively.
The OpenStack Key Manager service, known as Barbican, offers safe provisioning, storage, and administration of confidential data. Numerous services, including as Nova (Compute), Glance (Image), Cinder (Block Storage), and others, rely on Barbican.
The OpenStack Identity service known as Keystone offers distributed multi-tenant authorization, service discovery, and API client authentication. It is a fundamental part of OpenStack and is utilized for authentication and authorization by practically all other OpenStack services. Numerous services, like as Nova (Compute), Glance (Image), Neutron (Networking), Cinder (Block Storage), Swift (Object Storage), and others, are dependent on Keystone.
BARBICAN
A project within the OpenStack ecosystem called OpenStack Barbican is dedicated to offering secure key management services. To guarantee the security and confidentiality of sensitive information, it provides a number of security features. Key management and encryptionRed Hat OpenStack Platform: Why Use It?
The two primary areas that make up the value of Red Hat Management features are Service encryption management and Secrets management for infrastructure and tenant services like Cinder Volume Encryption, Cinder Backup Encryption, Swift Object Encryption, and Octavia Integration with Barbican.
OpenStack Barbican’s main security features are:
- Key Management and Storage users may store, retrieve, and manage cryptographic keys safely within the OpenStack environment thanks to its secure, centralized key management system. Keys are kept in a special repository for key storage, which may be supported by a safe database or an outside key management system.
- Significant Lifecycle Management allows key generation, rotation, and revocation throughout the key lifecycle. With the help of this functionality, keys are correctly managed over the course of their useful lives and can be quickly revoked or rotated if they become compromised.
- Access Management provides granular access control mechanisms to limit important processes and access. In order to set access policies based on user roles and permissions, it enables role-based access control (RBAC). This makes sure that only approved individuals or programs have access to and control over keys.
- Store keys safely uses several security techniques to safeguard keys while they are at rest. Before being stored, keys are encrypted, and access to the key storage repository is strictly regulated. Even if the underlying storage has been compromised, encryption aids in preventing unauthorized access to the keys.
- Logging and auditing provides the ability to log and audit critical management operations. This aids in monitoring and spotting any efforts at illegal access or dubious activity involving crucial procedures. Audit logs can be utilized for forensic investigation and compliance purposes.
- Discreet Communications through the use of secure protocols like Transport Layer Security (TLS), it makes sure that communication between the client applications and the key management server is safeguarded. This reduces the risk of eavesdropping and tampering while sensitive data is in transit.
- Keystone uses the authentication and permission features of OpenStack’s identity service. Barbican’s key management services can only be accessed by authenticated and authorized users or services thanks to this connection.
By adopting strong security controls and best practices, these security elements jointly improve the security of essential management processes in OpenStack systems and aid in protecting sensitive information.
Integration of Hardware Security Modules with Barbican
Hardware-based key protection techniques are supported by Barbican, such as the incorporation of Hardware Security Modules (HSMs). This makes it possible for keys to be managed and stored securely within specialized hardware units that offer tamper-resistant environments and carry out cryptographic operations. For sensitive data, including encryption keys, digital certificates, and other cryptographic assets, it offers a high level of safety.
OpenStack may use an HSM’s capabilities for key management and cryptographic operations by integrating it with OpenStack. The following are some crucial facets of OpenStack HSM integration:
- Key Administration integration enables OpenStack to delegate the HSM device’s administration of cryptographic keys. Keys are safely generated, stored, and guarded by the HSM, guaranteeing they are protected from unauthorized access
- Operations in Cryptography the HSM can be used by OpenStack to carry out cryptographic tasks such encryption, decryption, signature, and verification. High performance and greater security are provided for these tasks by the hardware-based cryptographic features of the HSM.
- Store keys safely to provide secure key storage environments that guard against physical and logical intrusions. The risk of key compromise is decreased by integrating HSMs with OpenStack because the keys used in the cloud infrastructure can be safely stored there.
- Auditing and Compliance offering a dependable platform for cryptographic operations, the provision of assistance with achieving regulatory compliance standards. By guaranteeing correct key management and protection, the HSM can help compliance with regulations such as PCI DSS (Payment Card Industry Data Security Standard) or FIPS (Federal Information Processing Standards).
KEYSTONE
To provide safe authentication, authorization, and access management, OpenStack Keystone, the identity service within the OpenStack ecosystem, contains a number of security measures. OpenStack Keystone offers several important features, including:
- Authentication token-based authentication, and external identity providers (like LDAP or Active Directory) are just a few of the techniques that is capable of supporting.
- Role-Based Access Control user permissions inside the OpenStack infrastructure. Only authorized users are given the proper access privileges because to RBAC’s ability to set fine-grained access restrictions based on user roles, projects, and domains.
- Using tokens for authorization issues tokens with information on the user’s identity and permissions after successful authentication. To approve access to OpenStack services and resources, Keystone verifies these tokens.
- Federation makes it possible to integrate with outside identity suppliers. With the help of this capability, users can log in to external systems and use their current login information to access OpenStack resources. While retaining security, federation streamlines user administration and expands possibilities for authentication.
- Endpoint Security uses Transport Layer Security (TLS) encryption for communication between clients and the Keystone service to ensure safe endpoint protection. By doing this, critical information communicated across the network is guaranteed to remain confidential and authentic.
- Logging and auditing monitor user authentication, authorisation, and policy enforcement operations, Keystone provides auditing and logging features. In order to monitor and identify potential security threats or unauthorized access attempts, audit logs give visibility into security-related events.
- Discreet Storage user information and passwords using the proper encryption techniques. This aids in preventing unwanted access to critical information even if the storage system is compromised.
- Authentication with many factors supports multi-factor authentication, which enables users to increase the security of their accounts by requiring extra authentication factors, such as one-time passwords (OTP) or biometric verification.
OpenStack Keystone supports the secure administration of user identities, authentication, and access control within the OpenStack system by integrating these security features. It aids in resource protection, data confidentiality, and the reduction of security concerns.
Everywhere transport layer security
Transport Layer Security Everywhere (TLS-e) is a crucial security component. Network traffic between OpenStack services is encrypted by default as part of a security initiative and is necessary to satisfy numerous regulating security agencies.
On overcloud endpoints in Red Hat OpenStack Platform, SSL/TLS is enabled. All elements of an OpenStack deployment, including internal traffic between services and external traffic from users to the OpenStack APIs, can communicate securely through it.
Red Hat OpenStack Platform 12 included this feature for external communications, and Red Hat OpenStack Platform 13 enabled it for all traffic. Red Hat OpenStack Platform’s simplicity of deployment for Director functionality is what distinguishes it from other platforms. Director connects with a Red Hat Identity Management (IdM) server to function as a certificate authority and manage the overcloud certificates for secure communication because the configuration of TLS everywhere necessitates a large number of certificates.
A secure SSL certificate
With Red Hat OpenStack Platform 16.1, we now support the generation of SSL certificates using private keys with a minimum key length of 2048 bits. The amount of the private keys used to generate certificates for encrypted service traffic can be increased by users to increase security. The minimum suggested size for private keys by the National Institute of Standards and Technology (NIST) is 2048 bits, which is the default for the Red Hat OpenStack Platform.