Configuration of EXTERNAL Vault in IBM App Connect
Here in this blog, we will learn about the Configuration of EXTERNAL Vault in IBM App Connect.
An EXTERNAL vault is a centralized repository for securely storing credentials and access tokens required for connecting to external services and applications. Unlike traditional methods where each integration server or node manages its own credentials, a shared vault allows multiple servers and nodes to access the same set of credentials. This not only enhances security but also simplifies credential management.
Configuration Methods
Configuring a shared vault can be achieved through various methods. One approach is to use the Connector Discovery wizard, which simplifies the process by guiding users through the setup. Alternatively, the mqsivault command-line tool provides advanced options for creating, modifying, or retrieving credentials from the vault. Users can also export and import vault contents for seamless migration.
Configuring a Shared Vault: –
Setting up a shared vault in IBM App Connect Enterprise for securely storing and managing credentials is essential for maintaining the integrity of your integration workflows. Follow these steps for the configuration:
- Create an Independent Integration Server Start by establishing an independent integration server.
- Deploy and Test Services Deploy your desired services on the server and rigorously test them. Confirm that the server functions correctly.
- Configure the IBM App Connect Enterprise Vault Use the ‘mqsivault’ command to initiate the configuration of an IBM App Connect Enterprise vault. This vault will store encrypted credentials for secure resource access. Ensure you’ve created the vault and specified the work directory.
Mqsivault –ext-vault-dir externalDirectoryVaultPath –create –ext-vault-key externalDirectoryVaultKey
- Define Vault Directory in YAML In your YAML configuration file, specify the directory where you created the vault. This step is crucial for the integration server to locate the encrypted credentials correctly:
Yamlfile –
Credentials:
ExternalDirectoryVault:
directory: ‘ externalDirectoryVaultPath ‘
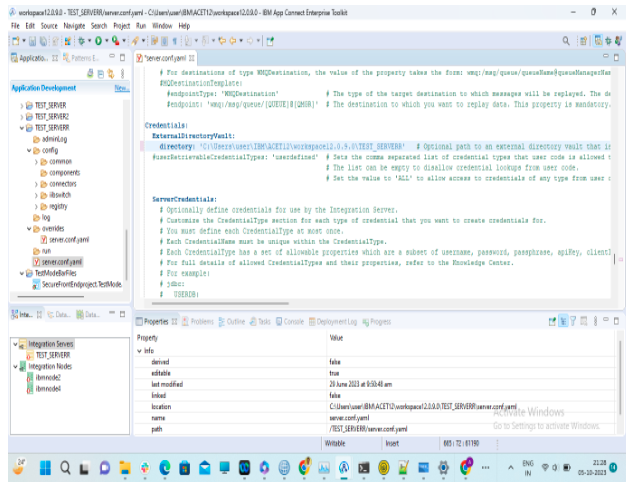
- Save Your YAML Configuration After adding the vault directory, save the YAML configuration file to preserve your changes.
- now , we can store credentials in external vault using mqsicredential command :
mqsicredentials –ext-vault-dir C:\Users\user\IBM\ACET12\workspace12.0.9.0\TEST_SERVERR –ext-vault-key vaultKey –credential-type type — credential-name name –username userName –password password –create
- Restart the Integration Server To enable seamless integration with the shared vault, restart the integration server. This action ensures that the server recognizes and utilizes the vault for secure resource access.








