SSL Implementation in IBM MQ Distribute Queue manager
Why SSL in IBM MQ?
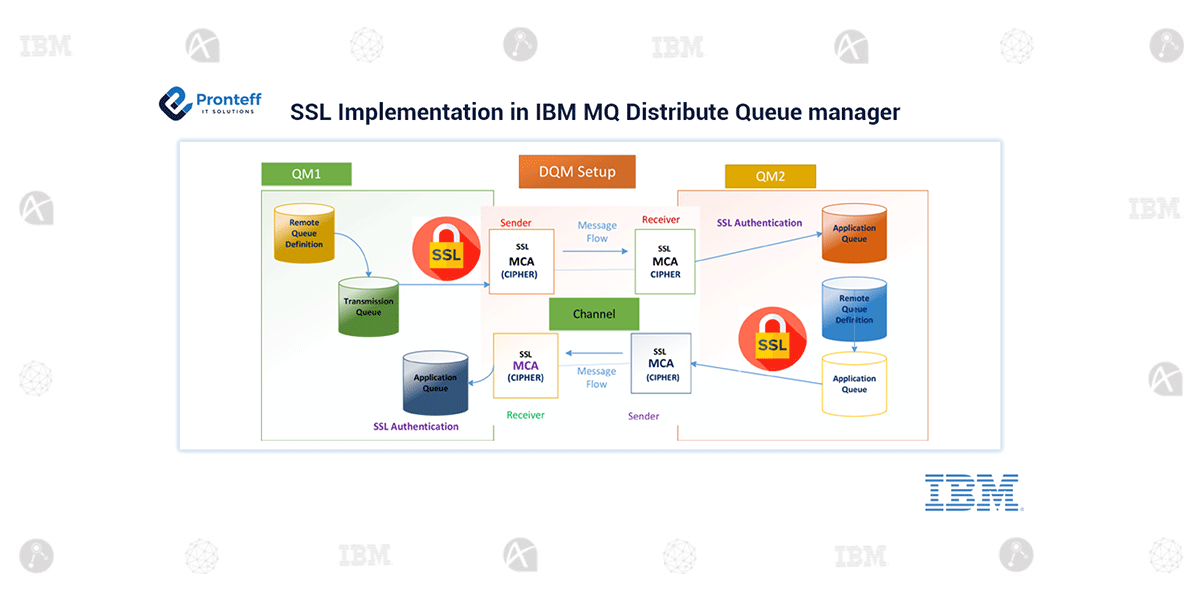
The SSL (Secure Socket Layer) protocol enables Queue Manager to communicate securely with another Queue Manager, or client.
Why SSL and TLS Security protocol in IBM MQ?
IBM MQ supports both the Transport Layer Security (TLS) and Secure Socket SSL (SSL) protocol to provide link-level security for message channel and MQI channels.
- Message channels and MQI channels can use the SSL or TLS protocol to provide link-level security. A caller MCA is an SSL or TLS client and a responder MCA is an SSL or TLS server. IBM MQ supports version 3.0 of the SSL protocol and version 1.0 and version 1.2 of the TLS protocol. You can specify the cryptographic algorithm that is used by the SSL or protocol by supplying a Cipher Spec as a part of the channel definition.
How does SSL Work in IBM MQ Server?
- When a queue manager connects to another queue manager, the two carry out a standard SSL exchange of certificates and carry out validation checks. If the validation is successful, the connection is established. To achieve this, you must configure both your queue managers and the channels that they will use, with appropriate certificate settings.
- When messages are sent from one queue manager to another queue manager along a channel, the data is generally encrypted using a session key that has been established during the certificate exchange. To achieve this, you must configure the channels that you will use with appropriate Cipher Specs.
- Secure communications that use the SSL or TLS cryptographic security protocols involve setting up the communication channels and managing the digital certificates that you will use for authentication.
- To set up your SSL or TLS installation you must define your channels to use SSL or TLS. You must also obtain and manage your digital certificates. On a test system, you can use self-signed certificates or certificates issued by a local certificate authority (CA). On a production system, do not use self-signed certificates.
- The SSL or TLS server always validates the client certificate if one is sent. If the client does not send a certificate, authentication fails only if the end of the channel that is acting as the SSL or TLS server is defined with either the SSLCAUTH parameter set to REQUIRED or an SSLPEER parameter value set.